Our internal CA issues certificates for our company to our Windows endpoints. They are all located in Certificates - Local Computer > Intermediate Certification Authorities > Certificates. We have many listed all with the same “Issued To” and “Issued By” name. The problem is that we are finding that these are causing issues with some internal applications. We would like to remove all that have expired leaving only the single “active” one. Any suggestions on how best to do this?
There are 2 distinct parts to any solution and they can be done independently.
- The most important thing to figure out is how to remove the problematic certificates on the command line NOT using bigfix.
- Don’t start with “How do I do this with BigFix?”
- Start with “How do I do this automatically without a GUI?” (command line)
- You really just need to know how to remove 1 of them, not all.
- Provide the working code here
- wrap it up in actionscript and test it through bigfix
- The next thing to figure out is how to detect that the problematic certificates exist using BigFix Relevance.
- This step is technically optional, but you should definitely endeavor to figure this out eventually so that you can detect when computers have this problem and when they no longer have this problem.
- I recommend starting with an analysis that reports actual data about the situation, not just a TRUE/FALSE value.
- The analysis and the data it collects will help determine the best way to turn that relevance into the best “applicability” relevance that returns a TRUE/FALSE value.
- How do they appear in the GUI?
- Can you provide (redacted) screenshots?
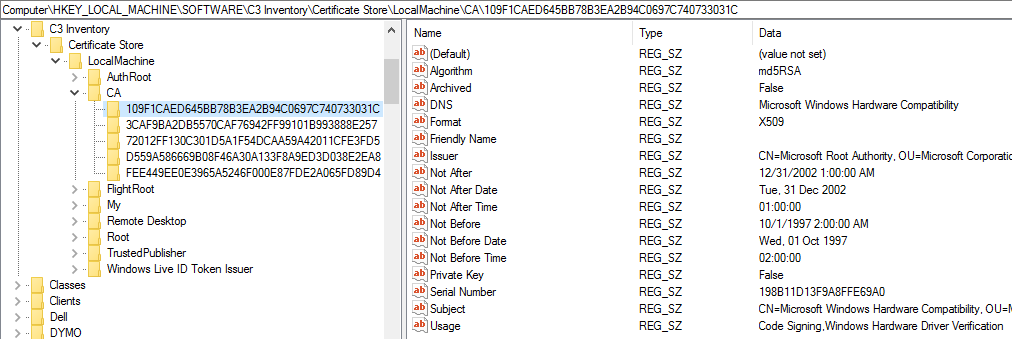
- Can you find the certs in the registry?
- Any commands that provide useful output related to this?
- Any websites or documentation you have found that seems related and useful?
I’ll see what I can dig up that I have related to this problem.
Related:
Thanks for your respose. We would be looking to remove all expired RR certs.
The Details of the cert has serial number, subject key id, thumbprint for example and I can’t link any of them to the string in the registry or to the Blog value (not that I can possible check that). I’m unsure how to use the info in the cert to find it in the registry.
I have a Certificate Store fixlet \ analysis pair:
Probe: On Github
Analysis: On Github
The Fixlet dumps the certificate store information to the registry and the Analysis reads it in.
You should be able to use this combination to write your own fixlet whose relevance uses the information in the registry and whose action script runs whatever command required to pull the certs.
Bill
Thanks. Though I know the BigFixMe Sync exists, I never looked into it. I’m setting it up now and it looks to be well worth while.