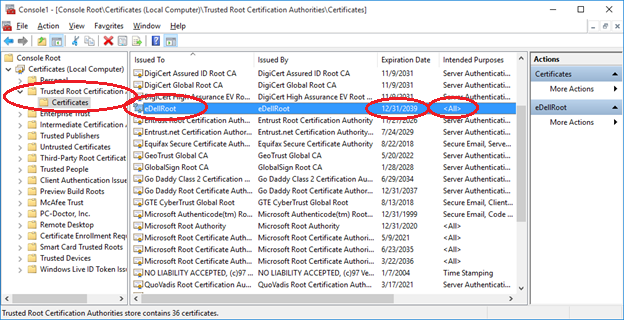
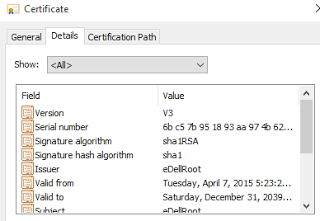
I’m actively working on BigFix content to detect and eventually remove the eDellRoot malicious Root Certificate.
Read more here: http://arstechnica.com/security/2015/11/dell-does-superfish-ships-pcs-with-self-signed-root-certificates/
Cert Thumbprint: (reddit)
98:A0:4E:41:63:35:77:90:C4:A7:9E:6D:71:3F:F0:AF:51:FE:69:27
Cert Serial Number: (reddit)
6b:c5:7b:95:18:93:aa:97:4b:62:4a:c0:88:fc:3b:b6
The following relevance SHOULD detect any certificate containing “eDellRoot”:
exists (hexadecimal string it) whose(it contains "eDellRoot") of ( unique values of (it as string) of values "blob" of keys of keys "Certificates" of keys whose(name of it as uppercase contains "CA" OR name of it as uppercase contains "ROOT") of keys "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates" of (x64 registries; x32 registries) )
The following session relevance should give the # of computers with “Dell Foundation Services” installed, which seems to be the source of this cert: https://bigfix.me/relevance/details/3003681
sum of multiplicities of unique values whose(it contains "Dell Foundation Services") of values of results of bes properties "Installed Applications - Windows"
The following session relevance should give the number of computers with the Dell Foundation Services windows service installed. Should match the number from the above session relevance:
sum of multiplicities of unique values whose(it contains "Dell Foundation Services") of values of results of bes properties "Services - Windows"
Names of Computers with “Dell Foundation Services” installed: https://bigfix.me/relevance/details/3003683
names of computers of results whose(exists values whose(it contains "Dell Foundation Services") of it) of bes properties "Installed Applications - Windows"
References:
- https://technet.microsoft.com/en-us/library/security/3119884.aspx
- https://www.reddit.com/r/technology/comments/3twmfv/dell_ships_laptops_with_rogue_root_ca_exactly/
- http://en.community.dell.com/dell-blogs/direct2dell/b/direct2dell/archive/2015/11/23/response-to-concerns-regarding-edellroot-certificate
- https://dellupdater.dell.com/Downloads/APP009/eDellRootCertificateRemovalInstructions.pdf
- http://www.zdnet.com/article/how-to-remove-dells-superfish-2-0-root-certificate-permanently/
- https://threatpost.com/dell-computers-ship-with-root-cert-private-key/115455/
- https://www.reddit.com/r/technology/comments/3twmfv/dell_ships_laptops_with_rogue_root_ca_exactly/
- http://blog.erratasec.com/2015/11/some-notes-on-edellroot-key.html
- New version of DFS: http://www.dell.com/support/home/us/en/19/Drivers/DriversDetails?driverId=77P24
- http://www.itninja.com/question/dell-system-detect-uninstallation-with-k1000#answer-97803
- http://www.itninja.com/question/detecting-edellroot-certificate-using-k1000
- http://www.itninja.com/question/edellroot-certificate-uninstall-using-k1000
- http://news.thewindowsclub.com/windows-defender-updates-definitions-remove-edellroot-80997/