The OpenSSL project has released the details on two vulnerabilities affecting OpenSSL 3.0.0 through 3.0.6 at [ Vulnerabilities ] - /news/vulnerabilities.html .
While last week’s pre-announcement indicated at least one of these would be Critical, the severity has since been downgraded to High based on mitigating factors.
https://cve.org/CVERecord?id=CVE-2022-3786
https://cve.org/CVERecord?id=CVE-2022-3602
Our understanding at this time is that the vulnerabilities affect OpenSSL when used in both client and server roles and there may be a range of affected products. OpenSSL is generally used in three ways -
- Installed as a system-wide library and used by applications (i.e. OpenSSL RPM or Debian Packages provided by the OS vendor)
- Delivered with a software application and used as a dynamic library (i.e. a product that delivers separate standalone libraries such as ‘libssl-3-X.so’ or ‘libssl-3-X.dll’
- Statically compiled into executable programs. In this case there are no standalone library files delivered, the OpenSSL code is incorporated directly into the program binary.
BigFix Response
-
There are no BigFix products affected by these vulnerabilities
-
We expect the operating system vendors to provide package updates shortly and will be delivering Fixlets for these updates through the normal patch sites.
-
We expect a number of application vendors will publish updated patches, and we will produce Fixlet content for supported products as they become available.
-
BigFix Inventory Signatures for detecting OpenSSL Libraries have been published to bigfix.me. See the detailed posting at How to use BigFix Inventory to discover applications that may be affected by OpenSSL vulnerability (CVE-2022-3786 and CVE-2022-3602) for more information.
-
We are working on Tasks and Analysis to perform scans of binary files on endpoints to detect the statically-compiled case. This content is detailed below.
-
We do not expect a simple detection based on network port probing, as was produced for the OpenSSL “HeartBleed” vulnerability in 2014. We are not currently investigating any network-based detection.
Binary Scanning Content
The BigFix team plans to publish content to scan endpoints and provide a listing of potentially-affected executable and library files. This scan is based on tooling from the YARA toolset, maintained by VirusTotal at GitHub - VirusTotal/yara: The pattern matching swiss knife
YARA is an advanced malware analysis tool that provides for inspecting files or system memory to look for defined signatures. In general use this is used to identify and classify new variants of malware, but is providing useful in this case for identifying the signatures of executable files and libraries compiled to use OpenSSL 3.
Initial publication will be made through the ‘Vulnerability Reporting’ site.
If you wish to test our pre-release content, you may do so at your own risk. The YARA content we are developing has the following known-issues, and may still contain unknown-issues at this point:
-
The YARA scan tool does not provide options for scan throttling.
– The only option available is to limit the number of threads used. Our test content has this limited to a single thread, which results in a longer scan time but may help to reduce system load somewhat. There is no option to limit processor or disk i/o usage, and we have observed high disk i/o during scans.
– Be sure to take care when executing scans, especially where those scans impact shared resources such as VM infrastructure or shared SAN resources. -
The YARA scan tool, on Windows, requires Visual C++ runtime installations. If not present or not at the current version, Visual C++ runtime libraries are installed as part of the scan task and remain installed on the system after the scan completes.
-
The Scan tasks have no Default Action, as care should be taken when schedule scans.
-
The Scan tasks have options in the Description tab to determine what should be scanned. By default all local filesystems are scanned. Optionally you may instead opt to scan only a specific subdirectory, which may be useful in testing specific products. Regardless of which option is selected, only the latest set of scan results is available for reporting.
-
YARA scan tasks for Linux and Mac are not yet available, but are in work. The main limitation being that we plan to compile and provide our own distribution of YARA for Linux and Mac. (The YARA project itself provides prebuilt binaries for Windows but not for Linux or Mac).
With those considerations, if you wish to test this pre-release content you may do so by importing and executing the Tasks and activating the Analysis at
-
Windows 32-bit Scan: OpenSSL 3.0.0 - 3.0.6 Detection - YARA Scan - Windows x32
-
Windows 64-bit Scan: OpenSSL 3.0.0 - 3.0.6 Detection - YARA Scan - Windows x64
-
Analysis Results: OpenSSL Scan Results (3.0.0 - 3.0.6)
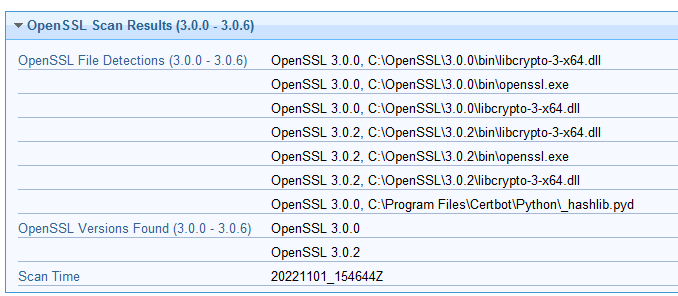
The Analysis provides three properties:
- OpenSSL File Detections (3.0.0 - 3.0.6) : A listing of detected OpenSSL version, and the file in which OpenSSL was found
- OpenSSL Versions Found (3.0.0 - 3.0.6): A listing of the unique OpenSSL versions that were found across all files on the scanned machine.
- Scan Time: The time at which the scan began executing, in format YYYYMMDD_HHMMSS UTC time.
Sample results below:
We welcome any & all feedback if you proceed with testing this pre-release content, and I appreciate your effort and patience as we all work to mitigate this issue.