Ah, certificates!
The WebUI CA-provided certificate we installed a year ago expired. No big deal, right?
1] Download renewed certificate.
2] Download current intermediary/root chain.
3] Combine them into a single file:
- Server certificate
- Intermediary(ies)
- Root Certificate
4] Rename the old file.
4] Copy the new file into the location of the old file, with the proper name.
5] Set new file’s permissions to match the older file.
6] Restart service.
Mon, 07 Feb 2022 21:51:10 -0800 -- WebUI service version 10.0.4.32 starting Mon, 07 Feb 2022 21:51:10 -0800 -- OpenSSL Initialized (Non-FIPS Mode) Mon, 07 Feb 2022 21:51:10 -0800 -- Using OpenSSL crypto library libBEScrypto64 - OpenSSL 1.0.2y 16 Feb 2021 Mon, 07 Feb 2022 21:51:10 -0800 -- [WebUI] Failed to retrieve all sites info from Root Server: HTTP Error 35: SSL connect error: error:140943F2:SSL routines:ssl3_read_bytes:sslv3 alert unexpected message Mon, 07 Feb 2022 21:51:11 -0800 -- [WebUI] Stopping WebUI service app Mon, 07 Feb 2022 21:51:22 -0800 -- [WebUI] Failed to update service application: HTTP Error 35: SSL connect error: error:140943F2:SSL routines:ssl3_read_bytes:sslv3 alert unexpected message
Any ideas from the hive mind? (No, there are no proxies anywhere. Really!)
“HTTP Error 35” seems to indicate a TLS negotiation error. Is there maybe something in the supported ciphers?
Infrastructure is on 10.0.4.
That looks like an error when it’s reaching out to the root server - did the root server’s certificate also change?
The only thing that changed yesterday was the WebUI’s CA SSL cert.
Probably should open a support incident and get some live help on it then. I’m in a call right now but I’d be checking on connectivity from the WebUI to the Root Server (which by the way will be connecting to root-server:52315 , not the normal 52311 you’d be seeing everywhere else)
I’ve seen that error message when we end up connecting to another process that has grabbed the port and isn’t HTTPS at all, on our WebUI loopback ports (Nutanix Guest Additions tends to grab port 5000 that WebUI is expecting to use). Maybe not the same, but I’d like to check that we can reach the Root Server’s webui api port anyway.
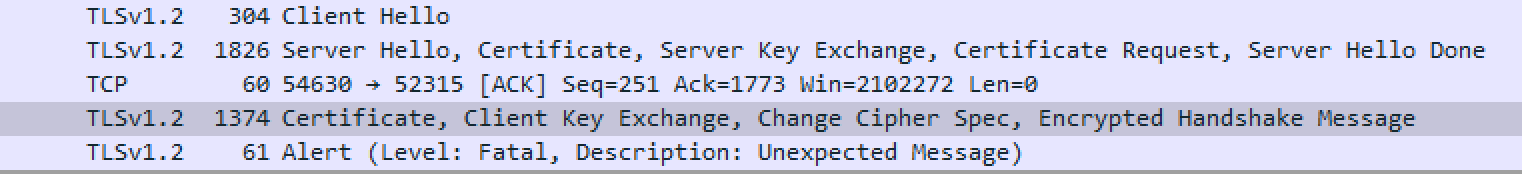
Wireshark shows that the connection to root:523115 is being made, but it dies in the TLS negotiation.
Neato. 
Hmmm. This document doesn’t use the word “renew” but states that WebUI should only use new private/public pairs.
https://support.hcltechsw.com/csm?id=kb_article&sysparm_article=KB0086478
After the old certificate for BigFix Web Reports or WebUI server expires, a new certificate must be created in order to access the mentioned sites via HTTPS. There are some instances that after applying the new certificate will cause Web Reports/WebUI not load properly.
TURNS OUT… WebUI doesn’t like it if you accidentally muck around inside of the certs subdirectory.
Stay safe, kids… only modify the files specified by your _WebUIAppEnv_WEB_CERT_FILE
and _WebUIAppEnv_WEB_KEY_FILE parameters.
3 Likes
Oh!..did you muck around in the ‘certs’ directory?
Yeah, those are …different. it contains the client auth cert that WebUI uses to authenticate to the root server.
They are normally generated by the WebUI Installation Fixlet…they can be rotated or replacements generated via BESAdmin, let me know if you need some help with that.