I am trying to create a simple task/fixlet that will just turn on Bitlocker for Windows 10 Pro devices that have bitlocker but isn’t on and drive is fully decrypted according to bigfix and what I can see on device itself. I have used @strawgate’s stuff he created but it shows not relevant for most of my devices in the previously described state.
Most computers come out of the box with TPM and other prerequisits for enabling bitlocker so just looking for a simple way to just turn it on using manage-bde or by changing the relevance on @strawgate’s fixlet.
I can then use all the analysis/probes/fixlets that @strawgate created to store the password and do other stuff.
Youll want to break apart the relevance of the enable bitlocker fixlet to see which statement is not relevant.
Once you determine which statement is returning false instead of true you can determine what needs to be done to enable encryption via BigFix.
I tried that, so to speak, by removing all relevance except Windows of operating system and targeted a test group. It seemed to work but some enpoints reported back that a reboot was required and some of them came back in a bitlocker recovery state but the password that bigfix knew about (and which was correct) was not valid and we had to rebuild some systems. I may need to dig into it more but I am a novice when it comes to relevance.
The stuff you created is great but could be updated to target computers that are coming from the factory with all the pre-requisits in place and bitlocker already enabled but waiting to be turned on. I am not sure what that would look like but assuming it has been done.
Thanks.
So what you’ll want to do is find a computer that you think should be relevant but isn’t and you’ll want to run each relevance statement individually until you find the relevance statement that is returning false.
The Fixlet should be relevant if Bitlocker is ready to go. There might be an edge-case the fixlet doesnt correctly detect but if you can’t test the individual relevance statements on a target device then I won’t be able to help you with a solution.
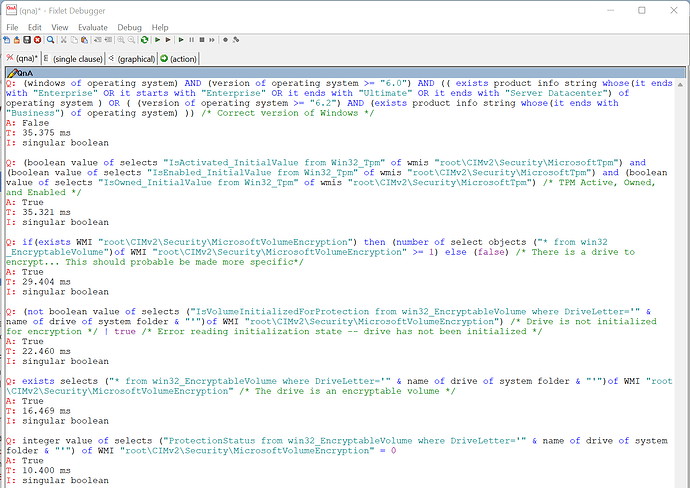
You’ll want to load Fixlet Debugger on a system and run each of these statements in Fixlet Debugger:
Q: (windows of operating system) AND (version of operating system >= "6.0") AND (( exists product info string whose(it ends with "Enterprise" OR it starts with "Enterprise" OR it ends with "Ultimate" OR it ends with "Server Datacenter") of operating system ) OR ( (version of operating system >= "6.2") AND (exists product info string whose(it ends with "Business") of operating system) )) /* Correct version of Windows */
Q: (boolean value of selects "IsActivated_InitialValue from Win32_Tpm" of wmis "root\CIMv2\Security\MicrosoftTpm") and (boolean value of selects "IsEnabled_InitialValue from Win32_Tpm" of wmis "root\CIMv2\Security\MicrosoftTpm") and (boolean value of selects "IsOwned_InitialValue from Win32_Tpm" of wmis "root\CIMv2\Security\MicrosoftTpm") /* TPM Active, Owned, and Enabled */
Q: if(exists WMI "root\CIMv2\Security\MicrosoftVolumeEncryption") then (number of select objects ("* from win32_EncryptableVolume")of WMI "root\CIMv2\Security\MicrosoftVolumeEncryption" >= 1) else (false) /* There is a drive to encrypt... This should probable be made more specific*/
Q: (not boolean value of selects ("IsVolumeInitializedForProtection from win32_EncryptableVolume where DriveLetter='" & name of drive of system folder & "'")of WMI "root\CIMv2\Security\MicrosoftVolumeEncryption") /* Drive is not initialized for encryption */ | true /* Error reading initialization state -- drive has not been initialized */
Q: exists selects ("* from win32_EncryptableVolume where DriveLetter='" & name of drive of system folder & "'")of WMI "root\CIMv2\Security\MicrosoftVolumeEncryption" /* The drive is an encryptable volume */
Q: integer value of selects ("ProtectionStatus from win32_EncryptableVolume where DriveLetter='" & name of drive of system folder & "'") of WMI "root\CIMv2\Security\MicrosoftVolumeEncryption" = 0
And then youll want to provide the result here. It’ll look something like this:
1 Like
This is great. I will do as you advise and let you know the results. Thank you so much.
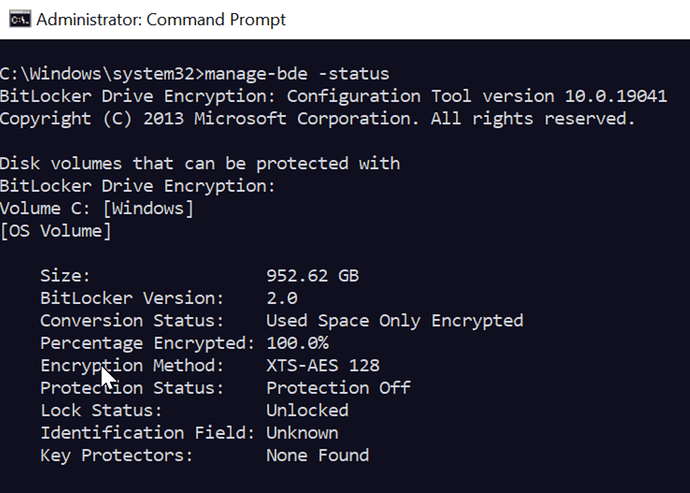
Ok. Here is some of my results from multiple test on different devices with different bitlocker status according to Bigfix. This was all very good information and has helped me understand your relevance and what it is doing. It appears that the relevance reporting False is because of TPM status and or whether the OS can see it. The last one I tested was actually against a drive that said it was encrypted but was not reporting a recovery password. I looked at that device and bitlocker hasn’t been turned on yet but the drive according to Bigfix says it is encrpyted. This may be the scenario I need to address going forward. How do I flip the switch on encrypted drives to turn on Bitlocker and report a password in Bigfix?
Results from S1376DTEST
Bitlocker Status = Fully Decrypted
TPM activated = Not Activated
TPM Visible to OS = False
BL Password = not reported
Relevance test =
Q:(boolean value of selects “IsActivated_InitialValue from Win32_Tpm” of wmis “root\CIMv2\Security\MicrosoftTpm”) and (boolean value of selects “IsEnabled_InitialValue from Win32_Tpm” of wmis “root\CIMv2\Security\MicrosoftTpm”) and (boolean value of selects “IsOwned_InitialValue from Win32_Tpm” of wmis “root\CIMv2\Security\MicrosoftTpm”) /* TPM Active, Owned, and Enabled */
E: Error: Singular expression refers to nonexistent object.
T: 15.000 ms
Results from S1284D
Bitlocker Status = Fully Decrypted
TPM activated = Activated
TPM Visible to OS = True
BL Password = not reported
Returned back true for everything in relevance
Results from 44SHIP
Bitlocker Status = Fully Decrypted
TPM activated = Not Activated
TPM Visible to OS = True
BL Password = Not reported
Relevance Test =
Q:(boolean value of selects “IsActivated_InitialValue from Win32_Tpm” of wmis “root\CIMv2\Security\MicrosoftTpm”) and (boolean value of selects “IsEnabled_InitialValue from Win32_Tpm” of wmis “root\CIMv2\Security\MicrosoftTpm”) and (boolean value of selects “IsOwned_InitialValue from Win32_Tpm” of wmis “root\CIMv2\Security\MicrosoftTpm”) /* TPM Active, Owned, and Enabled */
A: False
T: 163.000 ms
Results from S1256D
Bitlocker Status = Fully Decrypted
TPM activated = Activated
TPM Visible to OS = True
BL Password = Yes
Relevance Test = True for all relevance
Results from S4219L-W
Bitlocker Status = Fully Encrypted
TPM activated = Activated
TPM Visible to OS = True
BL Password = NO
Relevance Test =
Q:(not boolean value of selects (“IsVolumeInitializedForProtection from win32_EncryptableVolume where DriveLetter=’” & name of drive of system folder & “’”)of WMI “root\CIMv2\Security\MicrosoftVolumeEncryption”) /* Drive is not initialized for encryption / | true / Error reading initialization state – drive has not been initialized */
A: False
T: 57.000 ms
There is a setup guide for bitlocker in the GitHub repo here https://github.com/strawgate/C3-Protect/wiki/Bitlocker
If the TPM is present but not activated there is a fixlet you can use called, “Invoke - Provision Trusted Platform Module - Windows” you need to run first
If the TPM is not visible to the OS you need to configure it in UEFI/bios first.
For S4219L-W, the fixlet won’t be applicable if encryption is already enabled. For that device you’ll want to see what protectors are enabled with bitlocker. In the analysis called “Bitlocker - Key Protectors - Windows” there is a property called “Bitlocker - Recovery Password Enabled - Windows” does that return true for this device?
Or if you can get to the device you can check protectors with manage-bde -protectors -get and if you can run that and share the results I can provide some more insights.
2 Likes
Here is what Bigfix is telling me about that device. I don’t see a “Bitlocker - Key Protectors - Windows” analysis. I do see the Bitlocker Recovery Password - Windows property is that the same as the “Bitlocker - Recovery Password Enabled - Windows” property?
| Computer Name |
Bitlocker - Recovery Password - Windows |
Bitlocker - Status - Windows |
TPM - Visible to OS - Windows |
TPM - Activated in OS - Windows |
OS |
Last Report Time |
| S4219L-W |
not reported |
Fully Encrypted |
TRUE |
Activated |
Win10 10.0.19044.1645 (21H2) |
4/29/2022 13:31 |
I have seen the TPM fixlets you mentioned. I will see if I can get TPM activated using them on some of my endpoints that are reporting not activated or visible and then test the encryption fixlet on them.
I do see the Bitlocker Recovery Password - Windows property is that the same as the “Bitlocker - Recovery Password Enabled - Windows” property?
How did you obtain the content that you are missing an analysis? Do you have Show Non-Relevant Content checked in your BES Console?
The Bitlocker - Key Protectors - Windows analysis will report data after you’ve invoked the Invoke - Bitlocker Configuration Probe - Windows against the devices.
The property Bitlocker - Recovery Password Enabled - Windows tells you whether there is even a recovery password at all. The property Bitlocker - Recovery Password - Windows tells you what the recovery password is.
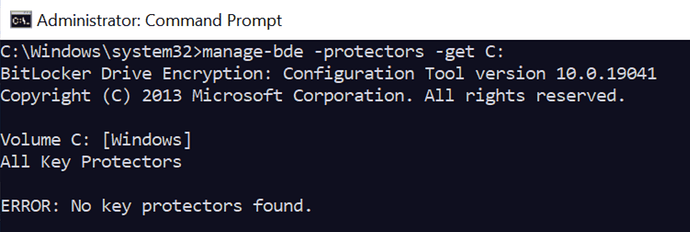
Can you please share the output from running manage-bde -protectors -get in an administrative command prompt on S4219L-W?
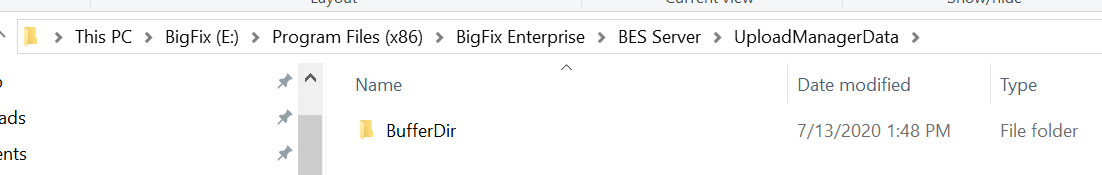
All logs related to Bitlocker encryption via the fixlets are uploaded to the BigFix root server using Upload Manager. You can find these logs here:
C:\Program Files (x86)\BigFix Enterprise\BES Server\UploadManagerData on your BigFix root server.
They will be in a directory based on the BigFix client ID. This will include the actual Bitlocker status, the recovery password and the log for how enabling encryption went.
I highly, highly recommend following the implementation guide here: Bitlocker · strawgate/C3-Protect Wiki · GitHub
1 Like
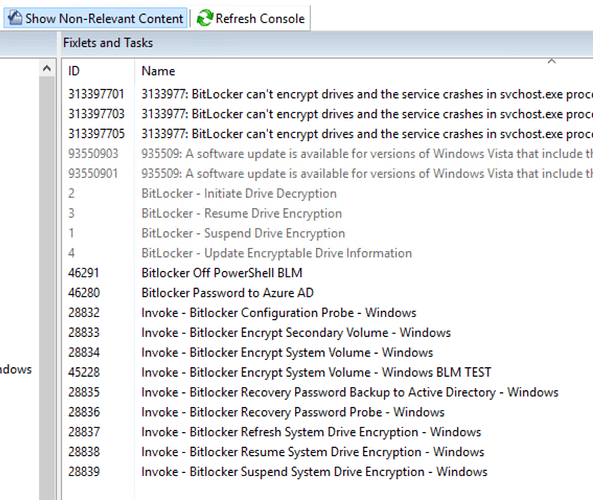
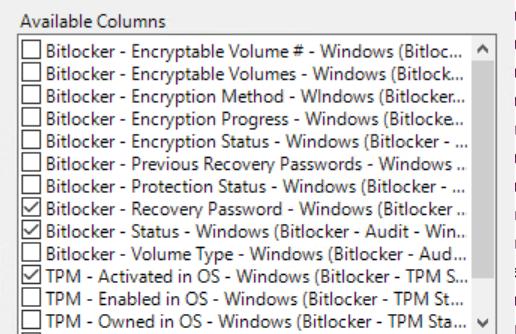
Here are all the bitlocker analysis I have. Some are not activated. Am I missing any? Should they all be activated?
Here are the available properties for Bitlocker that I have. Most if not all came from your content.
Changing Show Non-Relevant content doesn’t seem to reveal anything related to Bitlocker unless I am not looking in the right place.
I will try to get access to that laptop to run the manage-bde -protectors -get command tomorrow when I am physically in the office and share the output with you.
All I see in the C:\Program Files (x86)\BigFix Enterprise\BES Server\UploadManagerData on your BigFix root server, location is this below.
I followed an article by Brad Sexton to get most of this setup in the first place. It references your content almost exclusivly. I will look at the implementation guide you mentioned and see if there is anything there that I appear to be missing.
Again. Thanks for your help. I will keep feeding you information if you are willing to offer your assistance.
You requested this a few days ago and I am just getting access to the physical device.
I am still working on getting the anaylsis you suggested imported into my console.
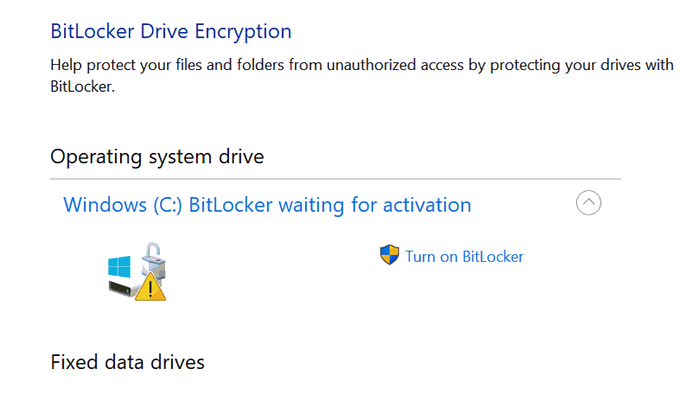
Here is a screenshot of the Bitlocker Manager status on that same device. I have assumed when I saw something with this status that the drive is encrypted but waiting for Bitlocker to be activated.
So it looks like encryption is enabled on the device but protection is not enabled which is why there are no key protectors and no recovery password.
Out of curiosity is the fixlet Invoke - Bitlocker Resume System Drive Encryption - Windows relevant on the device? Do you have that fixlet imported?
Yes I have that fixlet and yes that device is showing relevant for it.
I am trying to understand how devices running newer versions of windows 10 are configured by default. It seems like if they have all the pre-requsites in place such as TPM that even if you don’t turn on/activate or enable bitlocker that encryption happens and just sits there waiting for it to be enabled. To many words being used interchangeably gets a little confusing.
Explain to me then what the Resume, Refresh, and Suspend encryption is doing?
I am trying to understand how devices running newer versions of windows 10 are configured by default.
There is no requirement for how devices are configured by default and it will depend on the make, model, and configured features of the device.
With devices that shipped with Windows 7 it was very typical for the TPM to be disabled in the BIOS and need to be initialized in Windows before Bitlocker could be enabled.
With devices that ship with Windows 10 it is very typical for the TPM to be enabled and initialized and for there to be no other steps required to enable Bitlocker.
Explain to me then what the Resume, Refresh, and Suspend encryption is doing?
When you enable Bitlocker a decryption key is generated and stored on the hard drive in a way that only the TPM or the recovery password can decrypt.
When you pause Bitlocker, that key is then stored on the drive in an unencrypted fashion. This means that the data on the drive is still encrypted but the key to decrypt the data is available without needing the TPM or the recovery password. New data written to the disk is still encrypted.
When you resume Bitlocker, that key is then re-encrypted and then requires the TPM or the recovery password to decrypt.
The Invoke - Bitlocker Encrypt System Volume - Windows Fixlet starts bitlocker encryption for the drive.
The Invoke - Bitlocker Suspend System Drive Encryption - Windows Fixlet suspends/pauses bitlocker encryption
The Invoke - Bitlocker Resume System Drive Encryption 0 Windows Fixlet resumes bitlocker encryption.
Yes I have that fixlet and yes that device is showing relevant for it.
Protection is off for the device and so resuming encryption is required. The fixlets provided aren’t meant to cover every possible Bitlocker edge-case. I would recommend resuming encryption on that device and then checking the status on it to make sure Bitlocker was configured how you want it to be configured.
So I got the Bitlocker - Key Protectors analysis imported and activated and am showing the two new properties it created. Below is the results for the device we have been observing.
| Computer Name |
Bitlocker - Recovery Password Enabled - Windows |
Bitlocker - Encryption Status - Windows |
Bitlocker - Recovery Password - Windows |
Bitlocker - Protection Status - Windows |
Bitlocker - Status - Windows |
TPM - Owned in OS - Windows |
TPM - Activated in OS - Windows |
TPM - Visible to OS - Windows |
OS |
| S4219L-W |
not reported |
error |
not reported |
Protection Off |
Fully Encrypted |
Owned |
Activated |
TRUE |
Win10 10.0.19044.1645 (21H2) |
There are about 7 that report back the same for all of these properties. I can’t resume encryption on the one we have been observing just yet because of who the owner is. Not a good one to test on. So I am picking another that is from the list that reports the same and see what happens. I’ll let you know.
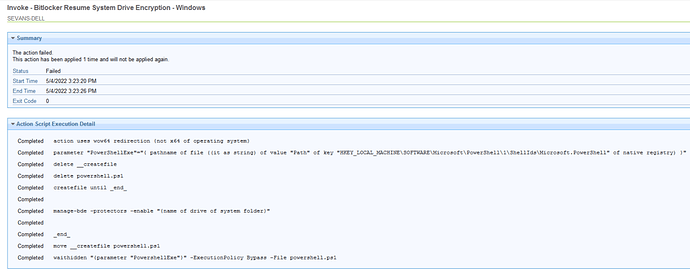
Here is the results of the Invoke - Bitlocker Resume System Drive Encryption - Windows for a device that had the same status as the S4219L-H that we had been observing.
Said everything completed and returned an exit code of 0 but status says Failed.
All that fixlet is doing is running manage-bde -protectors -enable "C:"
So you can run that on a test device and see what the error is and then you can figure out what you need to do to resolve it