First some tips:
Tip: If you are having problems simply seeing fixlets within the console, ensure you are properly toggling the two buttons named “Show Hidden Content” and “Show Non-Relevant Content” near the top of the console.
Tip: If you need to find all fixlets that are associated with specific CVE’s, you can create custom filters within the console to find these. For example: to pull in all fixlets associated with the following CVE’s (CVE-2017-5753, CVE-2017-5715, CVE-2017-5754), click on All Content > Fixlets and Tasks > Tools (on the menu) > Create Custom Filter and then set the filter similar to:
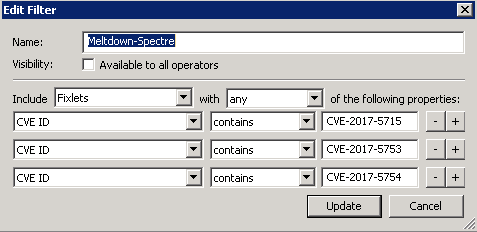
Continue building the filter to get to the specific fixlets you are looking for.
False Positive: The patch update is installed on the endpoint but the patch fixlet still shows as relevant for the endpoint in the console.
False Negative: The patch update is not installed on the endpoint and the patch fixlet shows not relevant for the endpoint in the console.
Preliminary Steps:
For both False Positive and False Negative scenarios take the following steps:
[1] Read the Descriptions of all the suspected problematic fixlet(s). There may be special notes of consideration in them to be aware of.
[2] Clear the BigFix console cache (http://www-01.ibm.com/support/docview.wss?uid=swg21505993) and restart the console. A stale cache in your console may be obscuring the current up-to-date view of your deployment. After clearing the cache and restarting the console check to see if the relevance problematic condition is still present.
[3] Check to ensure that the endpoint(s) you are investigating is/are subscribed to the Patches for Windows and Update for Windows Application sites. And, if you are making copies of the patching fixlets from these external sites to your custom sites ensure that your endpoints are subscribed to these custom sites as well. Some customers have a need to restrict the subscription of the Patches for Windows and Updates for Windows Applications external sites where only a set of Windows endpoints within their deployment are allowed to subscribe to these external sites. Generally, this is not the case and most customers choose to subscribe All computers to these sites and let the site level relevance take over in ensuring all Windows machines (and only Windows machines) subscribe to this site. Confirm the endpoints that are problematic are subscribed to these external sites.
[4] Check to see if the problematic endpoint(s) in question are in the state of Pending Restart (http://www-01.ibm.com/support/docview.wss?uid=swg21506002). You determine this easily by looking at the following set of fixlets within the BES Support site:
177 Restart Needed BES Support
391 Restart Needed - Not Triggered by a BES Action
390 Restart Needed - Triggered by a BES Action
If the endpoint is in a Pending Restart state, it may need to be restarted in order for the last updates that were applied to it to be finalized and for subsequent updates to evaluate as relevant. Restart any endpoints that are in a Pending Restart state and look over the patching fixlets again to determine if any are still needed and relevant.
[5] If the problematic fixlet has a KB associated with it, search within all the fixlets to find all fixlets associated with that KB. Are the other fixlets with the same associated KB relevant or not relevant on the problematic endpoints in question? For example, Microsoft has recently changed their update delivery methods in which they are now releasing larger updates: Cumulative Updates (CU) and Delta Updates (DU). BigFix develop has coded the CU’s to not be relevant when the DU’s are relevant and vice versa. This is to prevent some previously reported issues that had been reported when both CU and DU updates are being concurrently updated.
For example, searching for KB4056890 in the console returns the following fixlets 3 pairs, a pair for Win 2016, one for Win 10 32bit, and one for Win 10 64bit :
405689009 MS18-JAN: Cumulative update for Windows 10 Version 1607 - Windows 10 Version 1607 - KB4056890
405689005 MS18-JAN: Cumulative Update for Windows 10 Version 1607 - Windows 10 Version 1607 - KB4056890 (x64)
405689003 MS18-JAN: Cumulative Update for Windows Server 2016 - Windows Server 2016 - KB4056890 (x64)
405689011 MS18-JAN: Delta Update for Windows 10 Version 1607 - Windows 10 Version 1607 - Delta Update - KB4056890
405689007 MS18-JAN: Delta Update for Windows 10 Version 1607 - Windows 10 Version 1607 - Delta Update - KB4056890 (x64)
405689001 MS18-JAN: Delta Update for Windows Server 2016 - Windows Server 2016 - Delta Update - KB4056890 (x64)
For False Positive Issues:
Two scenarios may come up:
[1] The patch action indicates a successful installation in the console (action exit code = 0) and shows installed on the endpoint; but the patching fixlet still shows relevant again after reboot.
[2] The patch action indicates a failure to install (action exit code <> 0) and the patch shows as not installed on the endpoint; but the patching fixlet still shows relevant in the console.
In either case, it appears there may be a problem with either the initial evaluation or the evaluation after installation and reboot finalization in which at least one of the relevance statements in the fixlet is not evaluating to False as it should. All statements in the fixlet are incorrectly evaluating to True.
If the endpoint already has the patch update, the exit code returned in the Action Status, would typically indicate that, see the following installer error code meanings:
List of error codes and error messages for Windows Installer processes
– https://support.microsoft.com/en-us/kb/304888Windows Installer Error Messages
– Windows Installer Error Messages (for Developers) - Win32 apps | Microsoft LearnMsiExec.exe and InstMsi.exe Error Messages
– MsiExec.exe and InstMsi.exe error messages (for developers) - Win32 apps | Microsoft LearnError codes for Office 2010 update packages
– Error codes for Office 2010 update packages | Microsoft LearnWindows Update Agent Result Codes:
– Windows Update Agent Result Codes | Microsoft Learn [in hexadecimal]
– Common Windows Update errors - Windows Client | Microsoft Learn
– Windows Update Agent - Error Codes | Microsoft Learn
You can also attempt to install the update manually by downloading the installer from the download link which is found in the action script of the fixlet.
Download the update installer and attempt to run and install it on the endpoint. If the package is already installed, the installer dialog will return a message indicating it is already installed and not needed. This would confirm that there is an issue with the relevance and the relevance would need to be fixed by the BigFix Patches for Windows content development team. Open a support case with the following data as outlined below.
If it fails to install for some other reason, the error dialog will also indicate the reason. Look at the reason and see if you can determine why your machine may not be taking the patch. There may be an OS level issue on the endpoint machine that needs to be rectified before the patch can be applied.
For False Negative Issues:
At least one of the relevance statements in the fixlet is evaluating to False when in fact all should be evaluating to True. This expectation is based on your results from a check of the Windows Update Agent or MBSA scan from the endpoint(s).
Revisit the Preliminary Steps above and check to ensure all have been followed.
Data to Collect:
If the problem could not be resolved or if there is certainty that there is an issue with the relevance coding for which content development needs to address:
Collect the following data and open up a case with BigFix support:
[0] State whether the issue is a false positive or false negative and the scope (# of endpoints impacted)
[1] Fixlet ID(s), Name(s), and Site(s) of problematic fixlets
[2] QnA results of the problematic fixlet’s relevance statements using the Fixlet Debugger (http://www-01.ibm.com/support/docview.wss?uid=swg21966915)
[3] Outputs of the following commands from the command line on the problematic endpoint:
C:> systeminfo > sysinfo.txt (send the sysinfo.txt file)
C:> wmic qfe list > qfe_list.txt (send the qfe_list.txt file)
[4] MBSA results from the endpoint (https://www.microsoft.com/en-us/download/details.aspx?id=7558)
[5] Client Diagnostics (http://www-01.ibm.com/support/docview.wss?uid=swg21567025)
[6] An export of the registry keys the fixlet is checking during relevance evaluation, typically:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\NET Framework Setup\NDP" (For .Net fixlet only)
However, look at the relevance to see if any other keys are being evaluated and export those from the registry as well.