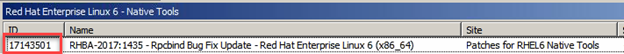
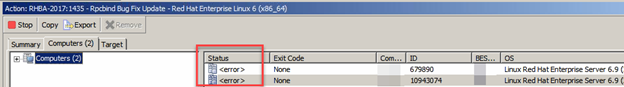
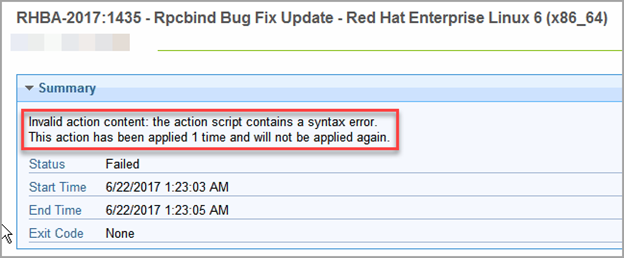
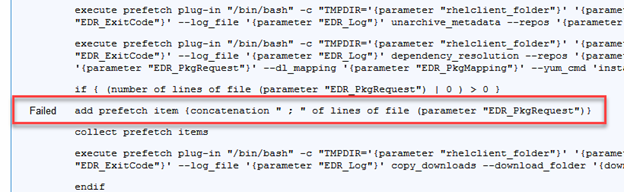
So the basic issue is that no matter which RHEL patch I deploy or what RHEL endpoint I deploy it to I am getting an action status of “error” surrounded by angle brackets (won’t display correctly on this page because they’re special html characters)
The environment:
-
I currently have an active RHEL subscription from which I can download patches for my red hat boxes. It’s a developer’s subscription which allows me to download patches for RHEL server
-
I have correctly configured the RHSM plugin in the BigFix Console. This means that I have:
a. Configured the plugin on the dashboard
b. Registered the system (the BF Server actually doing the download) in the acess.redhat.com site after loging in (I added it to the ‘registered systems’)
c. I downloaded all the certificates (entitlement cert / identity cert) into the “RHSMProtocol\certs\cert_set_1\” folder on the BigFix server (where the RHSM plugin is installed)
d. I’ve also enabled the GPG keys for the endpoints and I’ve extended the “plugin timeout"
The problem:
Every RHEL patch I try to send fails, but more than that: The failure registers in the BigFix console Action Status as “error”. However, I can see in the client log that it says “Ending Action” so I’m assuming it’s a failure. I’ve done some troubleshooting with no results:
a. Tested that my subscription gives me access to the specified patches. I did this two ways:
i. Run the RHSM plugin with the ‘–check-allrepos’ and ‘–check-baserepos’ argument (results were as I would have expected and are written in the RHSMPlugin.log file shared below)
ii. Registering the box itself with Red Hat and running a “yum update” directly from the computer. Once yum updated everything I went back into BigFix and the Fixlets that were relevant before no longer are relevant. So basically my subscription gives me access to the patches that BigFix is trying to install.
b. Re-installed the BigFix Client.
c. Created a brand new RHEL vm and installed nothing other than the BES Client
d. Tried with both a RHEL 6 and a RHEL 7 endpoint
e. (on edit): I found one of the packages this deployment was trying to download and was able to find it (and download it) in my ‘Entitled Repos’ by logging directly to redhat.com
And I’m sure I’m forgetting some other things I’ve tried because I’ve been troubleshooting this for a few days now.
So obviously my basic problem is that I can’t patch RHEL devices, but I don’t know why. I combed the logs, but the best I could find was this entry in the BESClient log:
ActionLogMessage: (action:4051) Missing required argument hashalgorithm=.
Note: hashalgorithm is surrounded by angle brackets.
I’ve searched for this everywhere, but I haven’t found an exact match and the one I did find here in the forum had the word ‘size’ instead of ‘hashalgorithm’ and it was resolved by upgrading the client (which I can’t do because I’m on the latest version).
Because I can’t attach text files here I’ve uploaded them to my Google Drive Public folder. Before copying them I cleared them all out from the endpoint so there would be no old data on there, then I re-ran the patch attempt:
https://drive.google.com/open?id=0Bz1wcOaAa2r8R3JRTHBrU3ZqX1E
(FYI: these are test systems in a lab so none of the data is really sensitive)
In the Shared folder are the following files:
• Client Log (20170618.log)
• The entire EDSDeployData folder (including the EDR_DeploymentResults.txt file)
• RHSM Plugin Log from the BES Server
Any help would be appreciated.
Regards,
M