Our BigFix admin is reluctant to enable the REST API and is spreading FUD about potential security issues. I have found plenty of documentation about using the REST API but haven’t found much documentation about the implementation details regarding security. Does anyone know where I can find something like that? I’m hoping for something that addresses details like the ones listed in the OWASP REST Cheat Sheet.
The REST API doesnt really let you do anything that console access wouldn’t let you do – I didnt realize you could turn off the REST API globally? Wouldnt all MOs have access anyway?
The REST API requires authentication in the same fashion as the console – it’s https if you have that enabled for your environment, there is access control in the same fashion as the console, and all of the questionable security choices that im aware of apply similarly to BigFix sessions in the console and the API.
And infact – if you know what you’re doing you can issue REST API calls from within a console session
Thanks Bill. I don’t do the admin side and am not a Master Operator, so when I say “enable” it’s probably more equivalent to “allow this user to use the REST API”. As you mentioned, I am also trying to explain to management that enabling use of the REST API is really no different (security-wise) from enabling someone to use the console. But my manager requested that I pose the question to the forums.
@steve, @aram, is there any official IBM documentation about the REST security for BigFix, or anything you feel might be relevant to the discussion?
All security models in the console also persist through the API. You as a non-MO can only effect the same endpoints/actions/content/etc that you can in the console. We use the console security to manage API security for our customers (desktop/server/etc) and it works very well. All the same security also persists over api/query calls as well. I have never seen non-MOs effect endpoints they don’t have access to in the console.
@sean, I’m not aware of any documentation that we have that speaks generally about the REST API security, but the comments made thus far certainly apply. The REST API is meant to facilitate automation of existing capabilities of the BigFix platform, and allows for the same sort of granular security controls as the Console does.
I would suggest that it would be helpful to have some context around the potential concerns, which should allow us to better address them (at this point, the question is very broad).
Thanks Aram, I agree and will be asking our admin what specifically he is concerned about. Thanks everyone for your help.
This is almost entirely true – there are some things related to console session which don’t apply via the REST API. For example, with regards to Dashboard variables (how dashboards and integrations store state within BigFix), the security model is implemented client side by the console and is thus not enforced at all via the REST API (a user with read-only access across the board but REST API access can write to this state store).
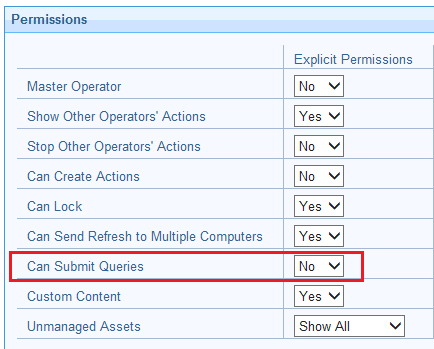
In addition, i believe there are certain endpoints like /query which allow functionality for a REST API user that you may not have intended (Fast Query). For example, most assume that you can only use BigFix query if you have WebUI and thus WebUI permissions but my understanding (may be incorrect) is that having REST API access alone allows you to submit fast queries.
I think your point on Fast Query is correct. I’m using the REST API to send and retrieve query results, and I don’t have WebUI installed at all.
Note of course that there is a permission bit for operators that allows you to control whether or not operators can submit queries: