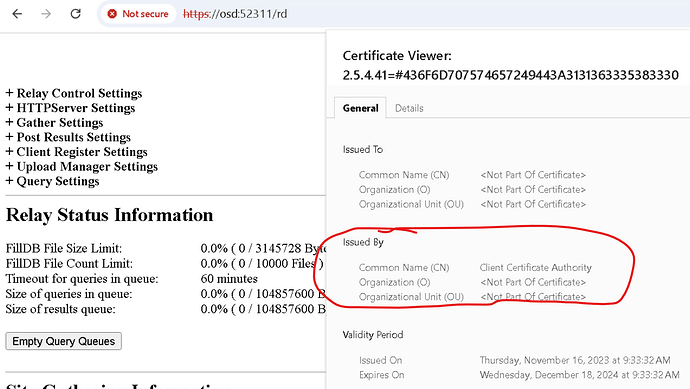
When we use a browser to open the Relay Diags page, the certificate is untrusted, but if we open it up and view the details we can see it’s issued by ‘Client Certificate Authority’. That ‘Client Certificate Authority’ is actually your BigFix Root Server, and is unique to your deployment (your ‘Client Certificate Authority’ is not the same as my ‘Client Certificate Authority’).
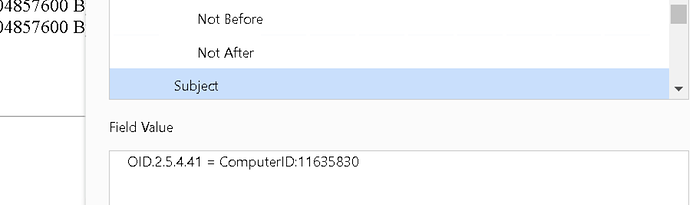
Further, it doesn’t have a ‘Common Name (CN)’. But if we go into the details and check the Subject, we can see it’s actually issued to a Bigfix ComputerID field, not to a hostname:
If we go to the Root Server, we can use BESAdmin to export the certificate chain (including your instance of ‘Client Certificate Authority’) :
C:\BES\Server>BESAdmin.exe /?
C:\BES\Server>mkdir \bes\certs\bes-bundle
C:\BES\Server>.\BESAdmin.exe /getcertificatebundle /bundleCertDir=c:\bes\certs\bes-bundle
C:\BES\Server>dir c:\bes\certs\bes-bundle
Volume in drive C has no label.
Volume Serial Number is C0BC-855F
Directory of c:\bes\certs\bes-bundle
01/14/2025 03:36 PM <DIR> .
01/14/2025 03:36 PM <DIR> ..
01/14/2025 03:36 PM 212,818 bundle.pem
1 File(s) 212,818 bytes
If we then use OpenSSL to verify the Relay using that bundle, it is successful:
openssl s_client -showcerts -connect osd.local:52311 -CAfile bundle.pem
C:\BES\certs\bes-bundle>openssl s_client -showcerts -connect osd.local:52311 -CAfile bundle.pem
CONNECTED(000001CC)
depth=4 C = US, ST = California, L = Emeryville, O = HCLTech, OU = Site Authorization, CN = Root Certificate, emailAddress = bigfix-security-team@hcl.com
verify return:1
depth=3 C = US, ST = California, O = HCLTech, OU = Site Authorization, CN = ActionSite Registrar:Secure License, emailAddress = bigfix-security-team@hcl.com
verify return:1
depth=2 C = US, <SNIP>
verify return:1
depth=1 CN = Client Certificate Authority
verify return:1
depth=0 name = ComputerID:11635830
verify return:1
---
Certificate chain
0 s:name = ComputerID:11635830
i:CN = Client Certificate Authority
a:PKEY: rsaEncryption, 2048 (bit); sigalg: RSA-SHA384
v:NotBefore: Jan 14 21:47:44 2025 GMT; NotAfter: Feb 16 21:47:44 2026 GMT
-----BEGIN CERTIFICATE-----
MIIDIjCCAgqgAwIBAgIEALGMdjANBgkqhkiG9w0BAQwFADAnMSUwIwYDVQQDExxD<SNIP>
-----END CERTIFICATE-----
1 s:CN = Client Certificate Authority
i:C = US, CN =<SNIP>
a:PKEY: rsaEncryption, 2048 (bit); sigalg: RSA-SHA384
v:NotBefore: Aug 11 16:23:22 2023 GMT; NotAfter: Aug 8 16:23:22 2033 GMT
-----BEGIN CERTIFICATE-----
MIIFVjCCAz6gAwIBAgIEv1x/gzANBgkqhkiG9w0BAQwFADCCAV8xCzAJBgNVBAYT<SNIP>
-----END CERTIFICATE-----
---
Server certificate
subject=name = ComputerID:11635830
issuer=CN = Client Certificate Authority
---
No client certificate CA names sent
Requested Signature Algorithms: ECDSA+SHA256:ECDSA+SHA384:ECDSA+SHA512:Ed25519:Ed448:RSA-PSS+SHA256:RSA-PSS+SHA384:RSA-PSS+SHA512:RSA-PSS+SHA256:RSA-PSS+SHA384:RSA-PSS+SHA512:RSA+SHA256:RSA+SHA384:RSA+SHA512:ECDSA+SHA224:RSA+SHA224
Shared Requested Signature Algorithms: ECDSA+SHA256:ECDSA+SHA384:ECDSA+SHA512:Ed25519:Ed448:RSA-PSS+SHA256:RSA-PSS+SHA384:RSA-PSS+SHA512:RSA-PSS+SHA256:RSA-PSS+SHA384:RSA-PSS+SHA512:RSA+SHA256:RSA+SHA384:RSA+SHA512
Peer signing digest: SHA256
Peer signature type: RSA-PSS
Server Temp Key: X25519, 253 bits
---
SSL handshake has read 2804 bytes and written 425 bytes
Verification: OK
---
New, TLSv1.3, Cipher is TLS_AES_256_GCM_SHA384
Server public key is 2048 bit
Secure Renegotiation IS NOT supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
Early data was not sent
Verify return code: 0 (ok)
---
That output shows that, given the bundle.pem exported by BESAdmin, OpenSSL can trust/validate the Relay certificate.
Getting Windows/Browser to trust the connection is more complicated. As far as I know, the Windows Certificate Manager client (the MSC graphical interface, or certutil.exe) don’t handle multiple certificates in a single PEM file. So I’ve had to extract each of those certificates to a separate file, numbered 1.pem through 6.pem in my case. Then I use certutil to import each of them into the ‘Trusted Root Authorities’ certificate store:
certutil –addstore -enterprise –f "Root" c:\bes\certs\bes-bundle\1.pem
certutil –addstore -enterprise –f "Root" c:\bes\certs\bes-bundle\2.pem
… and so on.
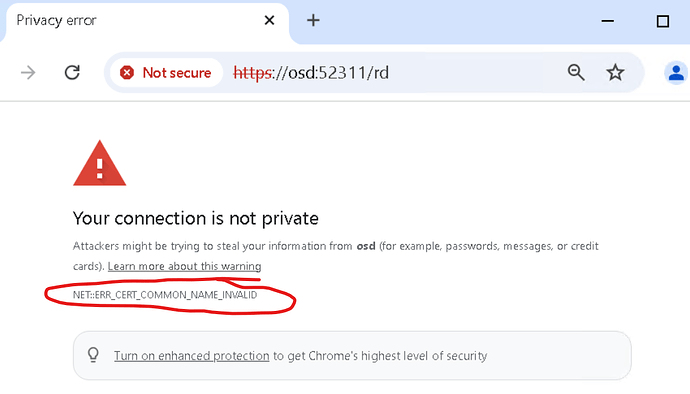
Then, restarting Chrome and browsing to the RD page, I get… another error!
This is different though - it’s not longer an ‘Untrusted Issuer’, now it’s a ‘COMMON_NAME_INVALID’ - which means there is no Hostname on the certificate matching the Relay hostname that I’m trying to browser. But I knew that, the certificate was issued to a BES ComputerID, and has no Subject or SubjectAltName entries with DNS hostnames in it.
And…according to Client certificate , it should have a SubjectAltName…but that starts in BigFix 11.0.3, and I see I never upgraded this Relay from 11.0.0, so I’ll run that upgrade and get back to you again.