Hello, everyone!
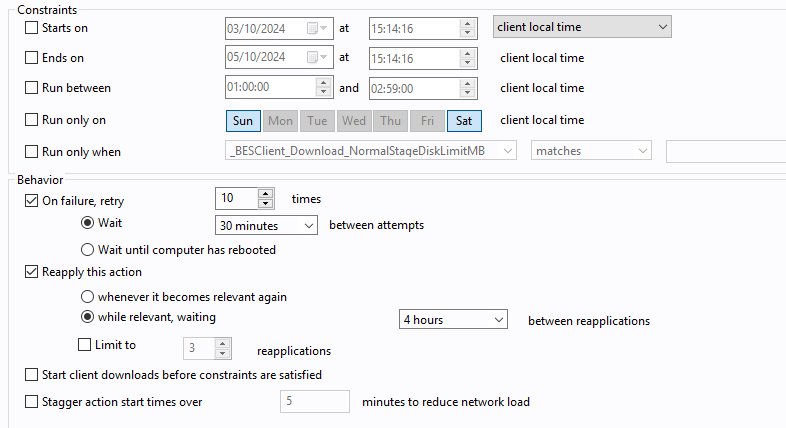
We have a Fixlet to update Windows Defender definitions every 4 hours (configured as a policy with no expiration date):
Below is the relevance we used:
(version of client >= "6.0.0.0") AND ((exists true whose (if true then (exists (operating system) whose (it as string as lowercase contains "Win2012" as lowercase)) else false)) OR (exists true whose (if true then (exists (operating system) whose (it as string as lowercase contains "Win2016" as lowercase)) else false)) OR (exists true whose (if true then (exists (operating system) whose (it as string as lowercase contains "Win2019" as lowercase)) else false)) OR (exists true whose (if true then (exists (operating system) whose (it as string as lowercase contains "Win2022" as lowercase)) else false)) OR (exists true whose (if true then (exists (operating system) whose (it as string as lowercase contains "Win8" as lowercase)) else false)) OR (exists true whose (if true then (exists (operating system) whose (it as string as lowercase contains "Win10" as lowercase)) else false)) OR (exists true whose (if true then (exists (operating system) whose (it as string as lowercase contains "Win11" as lowercase)) else false)))
And here is the ActionScript we are using:
begin prefetch block
// Download the x86 installer
add nohash prefetch item name=mpam-fe-x86.exe url=https://go.microsoft.com/fwlink/?LinkID=121721&arch=x86
// Download the x64 installer
add nohash prefetch item name=mpam-fe-x64.exe url=https://go.microsoft.com/fwlink/?LinkID=121721&arch=x64
end prefetch block
// Check if the OS is 64-bit and run the appropriate installer
if {x64 of operating system}
wait {download path "mpam-fe-x64.exe"} -q
else
wait {download path "mpam-fe-x86.exe"} -q
However, we’ve noticed that some machines are not updating as expected. For example, some machines were last updated on 09/26 but should have updated yesterday or today. Most machines are reporting correctly, but the update frequency remains a concern.
We have around 2200 relevant machines, divided into four groups:
- 1721 machines
- 208 machines
- 193 machines
- 54 machines
We would appreciate suggestions on how to optimize this policy to ensure that Windows Defender definitions are updated at least once or twice a day, ensuring more effective coverage.
Thank you in advance for your help!