(imported topic written by tscott91)
Hello, I was wondering if someone could help me create a report that would show the patches along with their description and file size for each patch Tuesday…
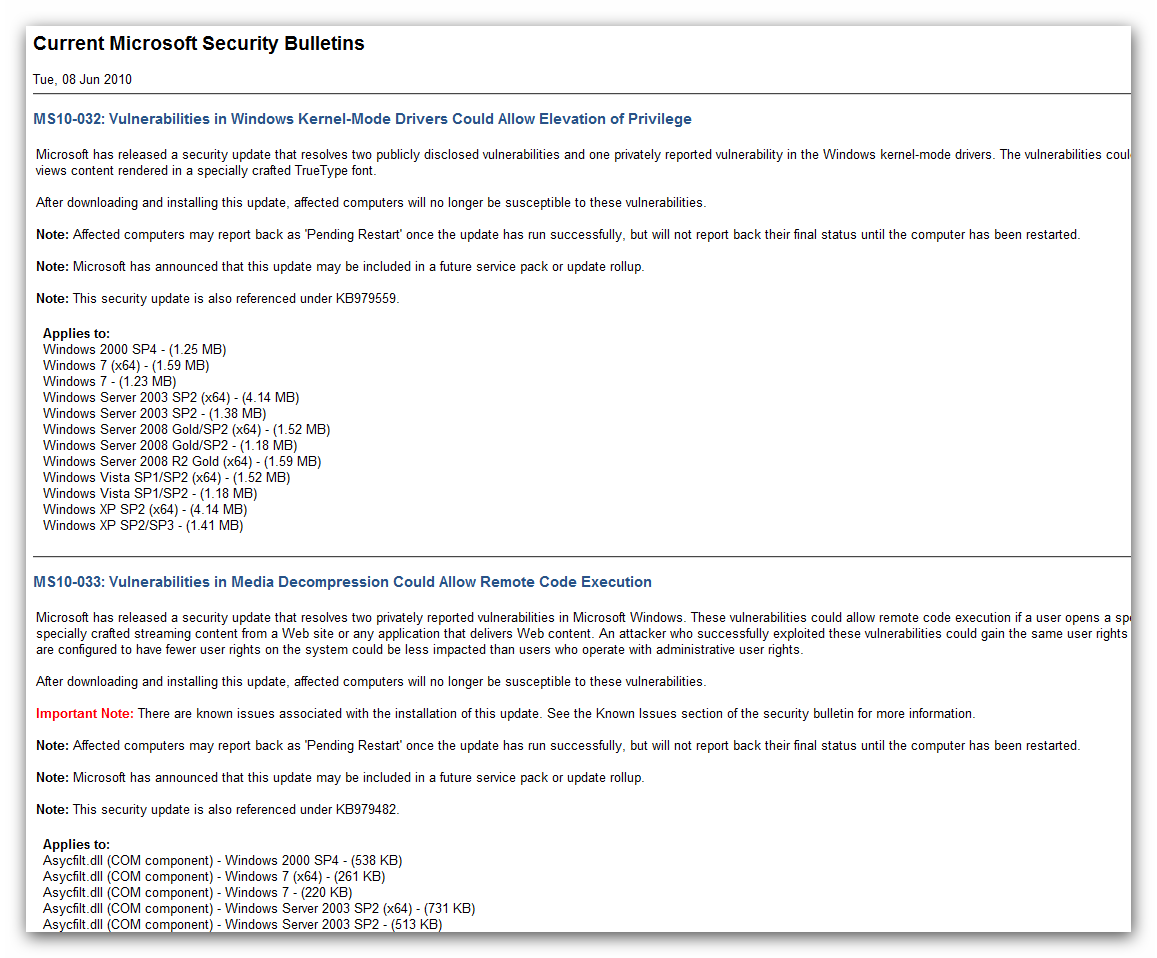
Basically I’m wanting something like this…
A drop down that has dates you can select (the patch Tuesday dates)… You select the date (IE: June 8th) and submit… Once submitted it has:
MS10-032: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege - Windows XP SP2/SP3
Description
Microsoft has released a security update that resolves two publicly disclosed vulnerabilities and one privately reported vulnerability in the Windows kernel-mode drivers. The vulnerabilities could allow elevation of privilege if a user views content rendered in a specially crafted TrueType font.
After downloading and installing this update, affected computers will no longer be susceptible to these vulnerabilities.
Note: Affected computers may report back as ‘Pending Restart’ once the update has run successfully, but will not report back their final status until the computer has been restarted.
Note: This security update is also referenced under KB979559.
File Size:
1.41 MB
MS10-033: Vulnerabilities in Media Decompression Could Allow Remote Code Execution - Quartz.dll (DirectShow) - Windows XP SP2/SP3
Description
Microsoft has released a security update that resolves two privately reported vulnerabilities in Microsoft Windows. These vulnerabilities could allow remote code execution if a user opens a specially crafted media file or receives specially crafted streaming content from a Web site or any application that delivers Web content. An attacker who successfully exploited these vulnerabilities could gain the same user rights as the local user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
After downloading and installing this update, affected computers will no longer be susceptible to these vulnerabilities.
Note: Affected computers may report back as ‘Pending Restart’ once the update has run successfully, but will not report back their final status until the computer has been restarted.
Note: Microsoft has announced that this update may be included in a future service pack or update rollup.
Note: This security update is also referenced under KB975562.
File Size:
1022 KB
And so on…
Reason I need something like this is we have a change control board and I have to manually copy / paste all this info in a doc to submit to them regarding any patches I install.
Thanks!