Grails framework applications that use grails data binding library version:
• >= 3.3.10 & < 3.3.15
• >= 4.0.0 & < 4.1.1
• >= 5.0.0 & < 5.1.9
• 5.2.0
are affected by CVE-2022-35912. Described on grails website:
“The vulnerability allows an attacker to remotely execute code within a Grails application runtime by issuing a specially crafted web request that grants the attacker access to the class loader. This attack exploits a section of the Grails data-binding logic. Grails data-binding is invoked in a number of ways including the creation of command objects, domain class construction, and manual data binding when using bindData. For a full description, please refer to the data-binding documentation.”
https://grails.org/blog/2022-07-18-rce-vulnerability.html
BigFix Inventory helps you to discover if the affected jars are deployed on your environment.
We have created 2 custom signatures to detect them:
• Signature which detects all of the versions of grails-databinding jar: https://bigfix.me/signature/details/1257
• Signature which detects versions of grails-databinding jar affected by the CVE (mentioned in the beginning of the article): https://bigfix.me/signature/details/1258
Using custom signatures for detecting grails-databinding jars:
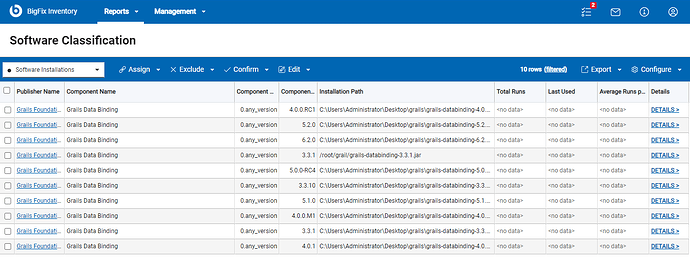
1. BigFix Inventory search for all grails-databinding-<version>.jar files
For generic audit, you can use a custom signature that searches on BigFix endpoints for JAR files that contain grails databinding file with names that fill pattern grails-databinding-<version>.jar.
After scanning your endpoints with this signature, BigFix Inventory will provide you with a report that contains information about all grails-databinding jar files, Regular component version displayed is 0.any_version and detailed version contains information about current patch level of this library
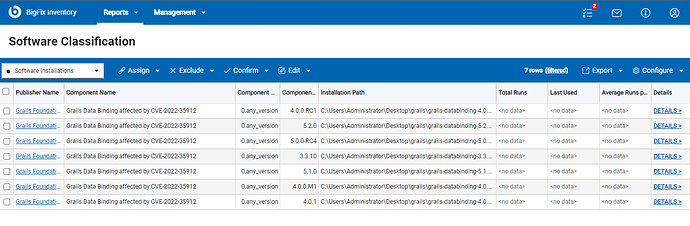
2. BigFix Inventory search for only affected grails-databinding-<version>.jar files
For a detailed auditing of CVE affected grails-databinding installations, BigFix Inventory provides an additional signature that searches for files with the patterns grails-databinding-<version>.jar and collects information about all occurrences of affected versions. Regular component version displayed after discovery is 0.any_version and detailed version contains information about current patch level of this library
The process for using both of custom signatures is the same:
- Download the signature file from URL provided under every type of discovery described.
- Login to BigFix Inventory.
- Go to Management → Catalog Customization.
- Import the file with the custom signature.
- Run an import process.
- Make sure that the catalog was propagated to the endpoints (automatically created action for propagation the endpoint executed on all applicable endpoints).
- Run a software scan on the endpoints.
- Ensure the Upload Software Scan Result fixlet is running.
- Run an import process to import the scan results.
- Verify the results on the reports.
Limitation: Results of scan are limited to jars which are stored directly in the file system, in case they are inside some other archive, they won’t be detected
Michal,
BigFix Inventory Team