That’s the result I got from the queries mentioned above:
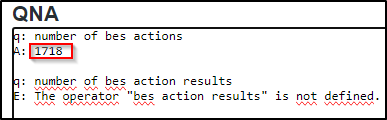
q: number of bes actions
A: 1718
q: number of results of bes actions
A: 52695
Now about this… I mean, I probably need to merge it better and do the proper modifications, I merged in the following way:
<!-- import jQuery -->
<script type="text/javascript" charset="utf8" src='https://code.jquery.com/jquery-3.4.1.js'></script>
<!-- import styles for dataTables and dataTables Buttons extension -->
<link rel="stylesheet" type="text/css" href="https://cdn.datatables.net/1.10.20/css/jquery.dataTables.css">
<link rel="stylesheet" type="text/css" href="https://cdn.datatables.net/buttons/1.6.1/css/buttons.dataTables.min.css">
<!-- import javascript for dataTables and dataTables Buttons extension -->
<script type="text/javascript" charset="utf8" src="https://cdn.datatables.net/1.10.20/js/jquery.dataTables.min.js"></script>
<script type="text/javascript" charset="utf8" src="https://cdn.datatables.net/buttons/1.6.1/js/dataTables.buttons.min.js"></script>
<script type="text/javascript" charset="utf8" src="https://cdn.datatables.net/buttons/1.6.1/js/buttons.flash.min.js"></script>
<script type="text/javascript" charset="utf8" src="https://cdnjs.cloudflare.com/ajax/libs/jszip/3.1.3/jszip.min.js"></script>
<script type="text/javascript" charset="utf8" src="https://cdnjs.cloudflare.com/ajax/libs/pdfmake/0.1.53/pdfmake.min.js"></script>
<script type="text/javascript" charset="utf8" src="https://cdnjs.cloudflare.com/ajax/libs/pdfmake/0.1.53/vfs_fonts.js"></script>
<script type="text/javascript" charset="utf8" src="https://cdn.datatables.net/buttons/1.6.1/js/buttons.html5.min.js"></script>
<script type="text/javascript" charset="utf8" src="https://cdn.datatables.net/buttons/1.6.1/js/buttons.print.min.js"></script>
<script>
$(document).ready(function() {
buildResults();
});
function buildResults() {
var table = $('#table1').DataTable( {
orderCellsTop: true,
fixedHeader: true,
autowidth: true,
paging: true,
//scrollX: true,
//scrollY: true,
"lengthMenu": [ [10, 25, 50, -1], [10, 25, 50, "All"] ],
dom: 'lBfrtlip',
buttons: [
{extend: 'copy', title: ''},
'csv',
{ extend: 'excel', title: ''},
'pdf', 'print'
],
} );
// Clone the header row so we can add search filters on each column
$('#table1 thead tr').clone(true).appendTo( '#table1 thead' );
$('#table1 thead tr:eq(1) th').each( function (i) {
var title = $(this).text();
$(this).html( '<input type="text" placeholder=" '+title+'" />' );
$( 'input', this ).on( 'keyup change', function () {
if ( table.column(i).search() !== this.value ) {
table
.column(i)
.search( this.value )
.draw();
}
} );
} );
table.draw();
document.getElementById("table1").style.visibility = "visible";
document.getElementById("table1").style.display= "inherit";
}
</script>
<style>
.header {
font-size: 14px;
background-color: #990000;
color: white;
padding: 6px 40px 6px 10px;
white-space: wrap;
}
.row {
font-size: 14px;
padding: 6px 40px 6px 10px;
border: 1px solid black;
border-top: none;
}
.nowrap {
white-space: nowrap;
}
</style>
<div id="seed_2" style="border: 5px solid #1976d2; border-top: none;">
<div style="background-color: #1976d2; color: white; padding: 5px 5px 5px 5px;">
</div>
<div style="padding: 20px; font-size: 18px; font-family: sans-serif; font-weight: 300;">
<div style="">
Action History Details
</div>
<div id="tableDiv" style="overflow:auto">
<table name='table1' id='table1' class='display' border='all' width="100%" style="visibility:hidden; display:none">
<thead>
<tr>
<th>Computer ID</th>
<th>Computer Name</th>
<th>Computer Groups</th>
<th>Parent Action ID</th>
<th>Parent Action Name</th>
<th>Action ID</th>
<th>Action Name</th>
<th>Issuer</th>
<th>Time Issued</th>
<th>Result</th>
<th>Exit Code</th>
<th>End Time</th>
<th>CVEs</th>
</tr>
</thead>
<tbody>
<?relevance
concatenation of trs of
(
concatenation "%0a"of (td of item 0 of it; td of item 1 of it; td of item 2 of it; td of item 3 of it;td of item 4 of it; td of item 5 of it; td of item 6 of it;td of item 7 of it;td of item 8 of it; td of item 9 of it; td of item 10 of it; td of item 11 of it)
) of
(
(
id of computer of it as string
, link of computer of it | "No Name" as html
, (if group member flag of action of it then link of parent group of action of it else "no parent" as html)
, id of action of it as string
, link of action of it
, name of issuer of action of it
, time issued of action of it as string
, state of action of it as string
, status of it as string
, exit code of it as string | "no exit code"
, end time of it as string | "no end time"
, cve id list of source fixlet of action of it as string| "no CVE"
) of results of it
;
(
if (exists targeted computer set of it) then /* retrieve properties for non-reported computer results */
(
id of item 0 of it as string /* non-reported computer id */
, link of item 0 of it | "<computer deleted>" as html
, (if group member flag of item 1 of it then link of parent group of item 1 of it else "" as html) | "" as html
, id of item 1 of it as string
, link of item 1 of it | "" as html
, name of issuer of item 1 of it | "no issuer"
, time issued of item 1 of it as string
, state of item 1 of it as string
, "Not Reported"
, "no exit code" /* exit code */
, "no end time" /* end time */
, cve id list of source fixlet of item 1 of it | "no CVE"
) of (elements of (targeted computer set of it - reported computer set of it), it ) else nothing
) of it
)
of bes actions
?>
</tbody>
</table>
</div>
</div>
</div>
Either it is getting too expensive, or it is not being able to display the results because of a mistake in the code.
**please if you need to redact anything, feel free.