When a specific version of dll or exe file is affected by a CVE, such as Telerik UI for ASP.NET version earlier than 2019.3.1023 affected by CVE-2019-18935, BigFix Inventory helps you to discover if the affected versions of the file are deployed in your environment.
This article describes two approaches to span an initial assessment to a detailed audit of affected library used in your environment using custom signatures. These custom signatures work without requiring to change the default BigFix Inventory behavior to gather additional data on .dll or exe files.
This approach can be used to detect any Windows dll or exe, you can customize the signature as required. Changing the signature definition to gather significant additional endpoint data, such as details of all *.dll files can create performance issues in production workloads and must be approached with caution.
1. Initial assessment - BigFix Inventory searches for all installations of selected dll or exe file
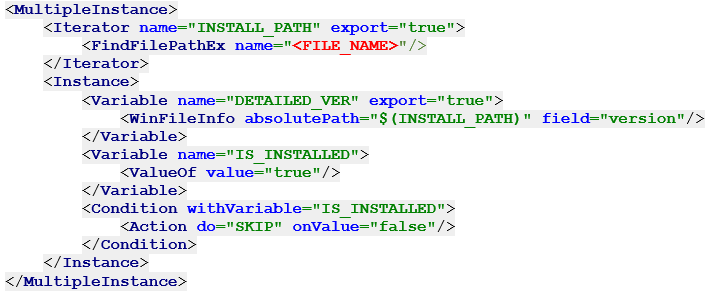
In the initial assessment, for a detailed auditing of selected dll or exe file installation, BigFix Inventory provides a signature that searches for given files information about all occurrences about them irrespective of their version. The signature provides a detailed version and the dll or exe and location information.
It is not recommended to create very wide search file patterns, such as *.dll or *.exe because it may significantly increase the volume of data sent over BigFix infrastructure and it will have a negative impact on the overall performance of the entire BigFix solution.
Check the signature definition below and update the <FILE_NAME> placeholder to search for a specific dll or exe file.
The signature for Telerik.Web.UI.dll is available at: https://www.bigfix.me/signature/details/1242.
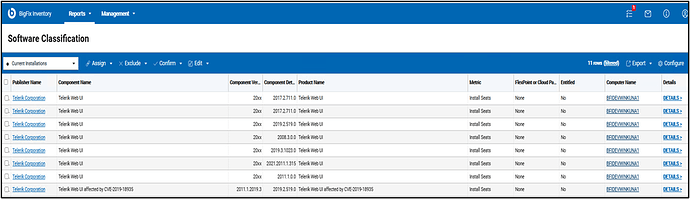
After scanning your endpoints with this signature, BigFix Inventory will provide you with a report that includes information about all Telerik Web UI libraries in your infrastructure.
2. Search for all affected DLL or EXE file installed version in selected range
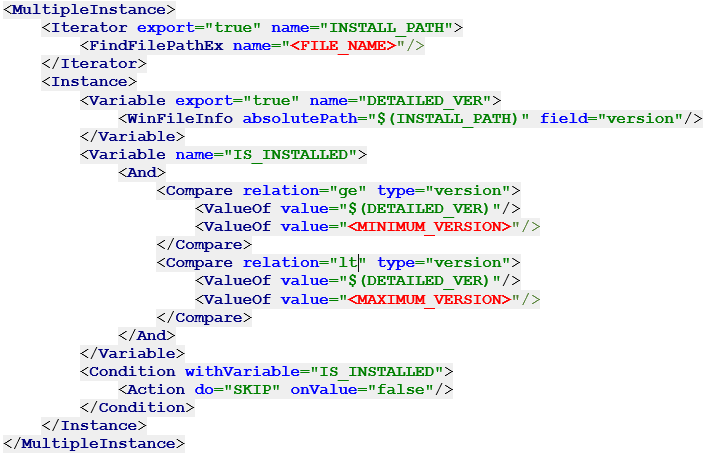
You can use a custom signature that searches on BigFix endpoints for DLL or EXE file with specific file name and version number between ranges vulnerable by a security issue,for example, Telerik.Web.UI.dll file that includes file version higher than 2011.1 and earlier than 2019.3.
Check the signature definition below and update the placeholder to search for a specific dll or exe file.
• <FILE_NAME> - specify file name
• <MINIMUM_VERSION > - specify the minimum version of file to be found
• <MAXIMUM_VERSION> - specify the maximum version of file to be found
The example signature for Telerik.Web.UI.dll is available at: https://www.bigfix.me/signature/details/1249
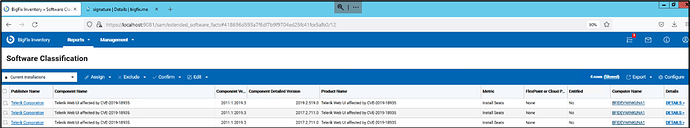
After you scan your endpoints with this signature, BigFix Inventory provides you with a report that includes information about discovery of the file, including detailed version of it as well as its location on the disk.
On the screenshot below you can view instances of the Telerik.Web.UI.dll files that include file version higher than 2011.1 and earlier than 2019.3 that were identified using the custom signature.
The process to use the custom CIT signatures is the same in both approaches. Perform the below steps to use the custom CIT signature:
- Download the signature file from URL provided under every type of discovery described.
- Login to BigFix Inventory.
- Go to Management → Catalog Customization.
- Import the file with the custom signature and customize as required.
- Run an import process.
- Make sure that the catalog was propagated to the endpoints (automatically created action for propagation the endpoint executed on all applicable endpoints).
- Run a software scan on the endpoints.
- Ensure the Upload Software Scan Result fixlet is running.
- Run an import process to import the scan results.
- Verify the results on the reports.