The following versions of MOVEit Transfer are affected by the mentioned CVEs:
-
CVE-2023-34362: In Progress MOVEit Transfer before 2021.0.6 (13.0.6), 2021.1.4 (13.1.4), 2022.0.4 (14.0.4), 2022.1.5 (14.1.5), and 2023.0.1 (15.0.1)
-
CVE-2023-35036: In Progress MOVEit Transfer before 2021.0.7 (13.0.7), 2021.1.5 (13.1.5), 2022.0.5 (14.0.5), 2022.1.6 (14.1.6), and 2023.0.2 (15.0.2)
-
CVE-2023-35708: In Progress MOVEit Transfer before 2021.0.8 (13.0.8), 2021.1.6 (13.1.6), 2022.0.6 (14.0.6), 2022.1.7 (14.1.7), and 2023.0.3 (15.0.3)
“SQL injection vulnerability has been found in the MOVEit Transfer web application that could allow an unauthenticated attacker to gain access to MOVEit Transfer’s database. Depending on the database engine being used (MySQL, Microsoft SQL Server, or Azure SQL), an attacker may be able to infer information about the structure and contents of the database, and execute SQL statements that alter or delete database elements. NOTE: this is exploited in the wild in May and June 2023; exploitation of unpatched systems can occur via HTTP or HTTPS. All versions (e.g., 2020.0 and 2019x) before the five explicitly mentioned versions are affected, including older unsupported versions.”
BigFix Inventory helps you to discover if the affected MOVEit transfer software installed on your environment.
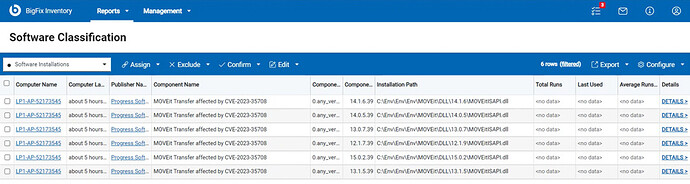
The signature with component name “MOVEit Transfer affected by CVE-2023-35708” specifically targets the versions of MOVEit Transfer affected by the mentioned CVEs. It helps identify the installed versions that are affected by the CVEs. You can find the signature at the following URL: https://bigfix.me/signature/details/1262
BigFix Inventory search for only affected versions of MOVEit transfer.
For a comprehensive audit of CVE affected MOVEit Transfer installations, Inventory offers an additional custom signature that searches for the MOVEitISAPI.dll file. This signature collects information about all instances of the affected versions. After discovery, the regular component version displayed is “0.any_version” while the detailed version includes information about the current patch level of the software.
If a user has applied a fix or patch to an existing setup, the signature based on the DLL file may not consider those versions as affected. The signature will detect the presence of the DLL file and provide information about the regular component version and the current patch level of the software. If the fix or patch has resolved the vulnerability, the affected status may no longer apply.
The process for using CIT custom signatures:
- Download the signature file from URL provided under every type of discovery described.
- Login to BigFix Inventory.
- Go to Management → Catalog Customization.
- Import the file with the custom signature.
- Run an import process to allow BFI server to process the signature and initiate the signature propagation to the endpoints.
- Run a software scan on the endpoints.
- Ensure the Upload Software Scan Result fixlet is running.
- Run an import process to import the scan results.
- Verify the results on the reports.
Raghavendra,
BigFix Inventory Team