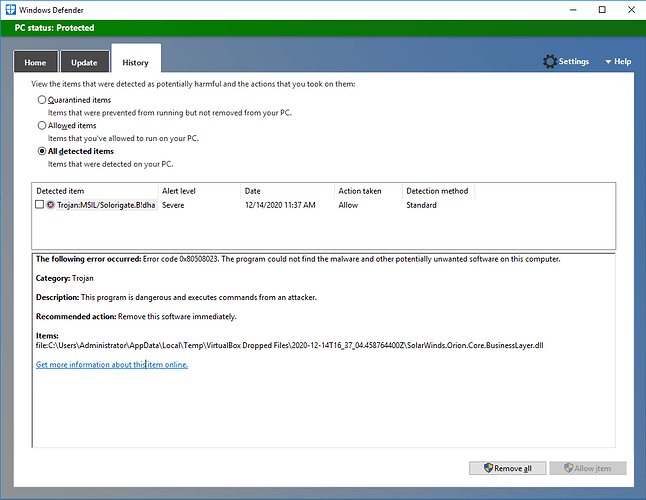
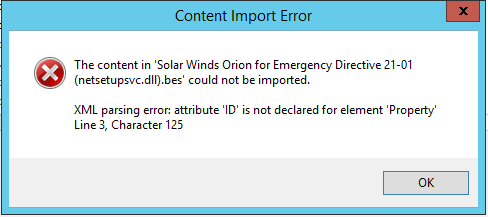
I’m starting this thread to track discussion of the US DHS Emergency Direction 21-01. Please try to keep discussion in this topic.
US Department of Homeland Security has identified an intrusion that appears related to the SolarWinds Orion product. Actions to take include shutting down SolarWinds devices, then scanning for several known Indicators of Compromise.
https://cyber.dhs.gov/ed/21-01/
Initial BETA IoC lists:
Method 1
https://bigfix.me/relevance/details/3023026 - search for SolarWinds.Orion.Core.BusinessLayer.dll and match hashes in several likely pathshttps://bigfix.me/relevance/details/3023027 - check for netsetupsvc.dll
Relevance to retrieve more details on detected files:
https://bigfix.me/relevance/details/3023028
The three above are pure Relevance. They can be queried using the BigFix Query app in BigFix WebUI, added as Properties, run in the Fixlet Debugger; but are not appropriate for direct export/import to the Console.
https://bigfix.me/analysis/details/2998622 is an Analysis containing the three properties of Method 1 that can be directly imported to into the Console.
Method 2
Alternate method: Full-disk scan for the files and retrieve the scan result via analysis
https://bigfix.me/fixlet/details/26725 - Scan Task
https://bigfix.me/analysis/details/2998618 - Analysis to retrieve results
(Analysis was just updated to include paths, size, modification time, version, md5, and sha1 of detected files)
Microsoft has also published guidance on this with additional compromised sha1 hashes and paths for the SolarWinds.Orion.Core.BusinessLayer.dll file. The Full-Disk Scan should find these files, and the additional hashes have been added to version 1.1 of the Analysis.
https://msrc-blog.microsoft.com/2020/12/13/customer-guidance-on-recent-nation-state-cyber-attacks/
The Full-Disk analysis just updated with additional known-bad sha256 hashes, 2020-12-14 14:45 CST, v1.2
2020-12-16 12:21 pm CST: Updated the “Method 1” Analysis to also attempt retrieving SolarWinds Orion installation path from Add/Remove Programs registry keys, and to report installation details if SolarWinds Orion is found in the Registry.
2020-12-16 13:21 CST: Updated https://bigfix.me/analysis/details/2998624 to retrieve “unique values” for the file details. The same file could be reported twice if installed in a default installation path (found in both the “assumed paths to check” and the “installation path from registry”)
2020-12-17 10:20 CST - Updated https://bigfix.me/analysis/details/2998625 to correct a false-negative due to redirected 32-bit file paths.
2020-12-17 12:00 CST - Updated https://bigfix.me/analysis/details/2998625 to correct an issue with older BigFix clients lacking the ‘locked line of file’ inspector, and to remove three erroneous hashes as pointed out by @sbl.
2020-12-21 10:21 AM CST - A separate vulnerability SolarWinds has been identified, dubbed ‘SuperNova’. MSRC has also updated list of sha256 hashes for Sunburst vulnerability. Method 1 Analysis, and Method 2 Task and Analysis have been updated at BigFix.me
Related:
- https://cyber.dhs.gov/ed/21-01/
- https://msrc-blog.microsoft.com/2020/12/13/customer-guidance-on-recent-nation-state-cyber-attacks/
- https://www.solarwinds.com/certadvisory
- https://www.sans.org/webcasts/emergency-webcast-about-solarwinds-supply-chain-attack-118015
- https://github.com/fireeye/sunburst_countermeasures
- https://www.sans.org/webcasts/emergency-webcast-about-solarwinds-supply-chain-attack-118015
- MS-ISAC Advisory 2020-166
- CVE-2020-14005
- CVE-2020-13169
- https://unit42.paloaltonetworks.com/solarstorm-supernova/