All,
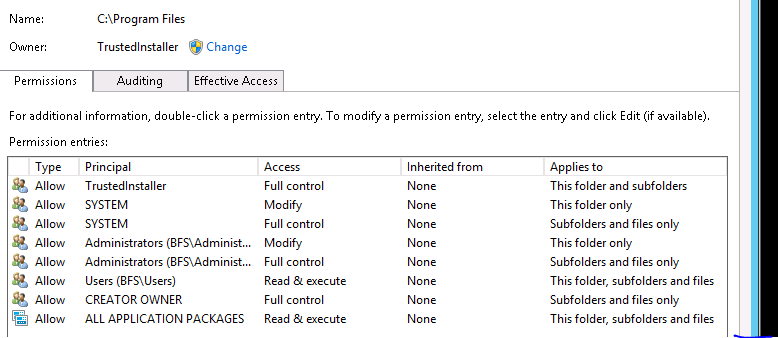
I want to get account name and permission of CREATOR OWNER but still stuck on some issue that I can’t query it. I found that it applied to subfolder and file only.
If you observe closely, CREATER OWNER permissions only apply to subfolders and files. So that is the reason it is not coming up. There are 2 entries for Administrators and SYSTEM as well where one of the entry is similar to the creator owner.
If you want CREATOR OWNER to show up then add these properties
inherit only of it, object inherit of it, container inherit of it,
Can you please provide a copy-paste of the relevance text in the bottom of the post? This will help myself & others grab where your at and test / add to it more easily. The screenshots are definitely useful, but the text is extremely helpful.
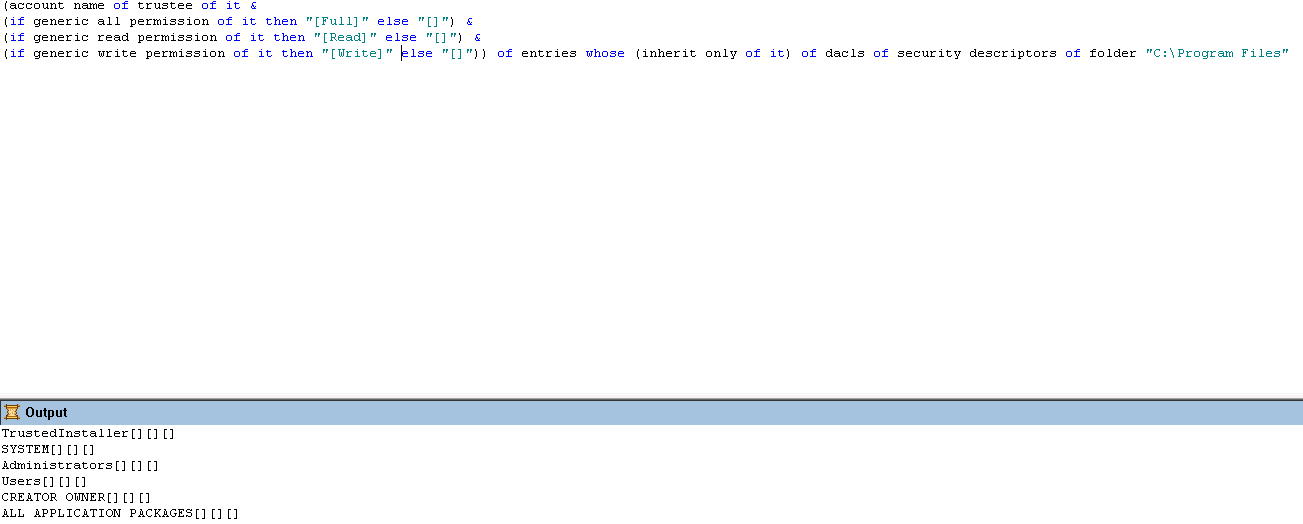
Thank you for your reply. I’ve tried to put “inherit only of it” as text under below. It show the account name creator owner, but still no permission shown.
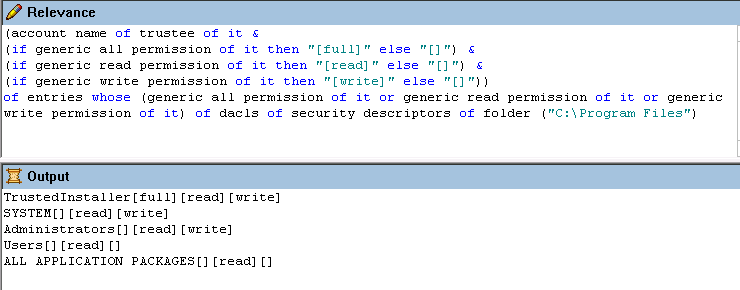
Relevance :
(account name of trustee of it &
(if generic all permission of it then “[Full]” else “”) &
(if generic read permission of it then “[Read]” else “”) &
(if generic write permission of it then “[Write]” else “”)) of entries whose (inherit only of it) of dacls of security descriptors of folder “C:\Program Files”
I think you’re filtering out all the values for which you are searching. Have a look at the properties of an access control entry:
q: properties of type "access control entry"
A: read permission of <access control entry>: boolean
A: list permission of <access control entry>: boolean
A: write permission of <access control entry>: boolean
A: create file permission of <access control entry>: boolean
A: append permission of <access control entry>: boolean
A: create folder permission of <access control entry>: boolean
A: read extended attributes permission of <access control entry>: boolean
A: write extended attributes permission of <access control entry>: boolean
A: execute permission of <access control entry>: boolean
A: traverse permission of <access control entry>: boolean
A: delete child permission of <access control entry>: boolean
A: read attributes permission of <access control entry>: boolean
A: write attributes permission of <access control entry>: boolean
A: query value permission of <access control entry>: boolean
A: set value permission of <access control entry>: boolean
A: create subkey permission of <access control entry>: boolean
A: enumerate subkeys permission of <access control entry>: boolean
A: change notification permission of <access control entry>: boolean
A: create link permission of <access control entry>: boolean
A: delete permission of <access control entry>: boolean
A: read control permission of <access control entry>: boolean
A: write dac permission of <access control entry>: boolean
A: write owner permission of <access control entry>: boolean
A: synchronize permission of <access control entry>: boolean
A: access system security permission of <access control entry>: boolean
A: maximum allowed permission of <access control entry>: boolean
A: generic all permission of <access control entry>: boolean
A: generic execute permission of <access control entry>: boolean
A: generic write permission of <access control entry>: boolean
A: generic read permission of <access control entry>: boolean
A: access mode of <access control entry>: integer
A: grant type of <access control entry>: boolean
A: deny type of <access control entry>: boolean
A: audit success of <access control entry>: boolean
A: audit failure of <access control entry>: boolean
A: object inherit of <access control entry>: boolean
A: container inherit of <access control entry>: boolean
A: no propagate inherit of <access control entry>: boolean
A: inherit only of <access control entry>: boolean
A: inherited of <access control entry>: boolean
A: inheritance of <access control entry>: integer
A: ace flag of <access control entry>: integer
A: ace type of <access control entry>: integer
A: trustee type of <access control entry>: integer
A: trustee of <access control entry>: security identifier
T: 0.498 ms
I: plural property
I’d start by pulling a full list of values, and then try to apply whatever filters you like afterward. Something similar to
q: (trustee of it, generic all permission of it, generic read permission of it, generic write permission of it, inherit only of it) of entries of dacls of security descriptors of folder "C:\Program Files"
A: NT SERVICE\TrustedInstaller, True, True, True, False
A: NT SERVICE\TrustedInstaller, False, False, False, True
A: NT AUTHORITY\SYSTEM, False, True, True, False
A: NT AUTHORITY\SYSTEM, False, False, False, True
A: BUILTIN\Administrators, False, True, True, False
A: BUILTIN\Administrators, False, False, False, True
A: BUILTIN\Users, False, True, False, False
A: BUILTIN\Users, False, False, False, True
A: CREATOR OWNER, False, False, False, True
A: APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES, False, True, False, False
A: APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES, False, False, False, True
A: APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES, False, True, False, False
A: APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES, False, False, False, True
T: 6.405 ms
I: plural ( security identifier, boolean, boolean, boolean, boolean )
I believe mine are the default permissions, and as you can see none of the “inherit only” entries actually grant any accesses to the folder (the folder permissions are granted on the “not inherit only” entries).
This is a very old post, but I am trying to do a related query, and cannot figure out what I am doing wrong. Basically for trustee “Authenticated Users” I want to check if Deny is set on advanced options. I can query for example
Q: (trustee of it, generic write permission of it, deny type of it) of entries of dacls of security descriptors of folder “c:\IBM\ITM”
A: NT AUTHORITY\Authenticated Users, False, True
A: NT AUTHORITY\SYSTEM, True, False
A: BUILTIN\Administrators, True, False
A: BUILTIN\Users, False, False
A: BUILTIN\Users, False, False
A: BUILTIN\Users, False, False
A: CREATOR OWNER, False, False
T: 7685
I can also check to see if generic write permission is set for Authenticated users:
Q: exists it whose(it = TRUE) of effective write permissions for “Authenticated Users” of dacls of security descriptors of folder “c:\IBM\ITM”
A: False
T: 22350
but how can I query for “deny type” ? I was not sure of the syntax so tried “effective deny type”, “deny type”, but whichever I try I get that the operator is not defined. Basically I need to query all of the Bigfix endpoints to see if on folder c:\IBM\ITM the Authenticated Users is set to Deny. This is one example I have tried but obviously am using the incorrect operator.
Q: exists it whose(it = TRUE) of deny type for “Authenticated Users” of dacls of security descriptors of folder “c:\IBM\ITM”
E: The operator “deny type for” is not defined.
I can’t test now but probably need to check the ‘ace type’ see https://developer.bigfix.com/relevance/reference/access-control-entry.html
Jason thank you so much. I had two issues, one that I was using the wrong value, and secondly I was struggling a bit with my code as I have not written very much relevance.
This is what I ended up with.
exists (ace type of it) of entries whose (trustee of it as string = “NT AUTHORITY\Authenticated Users” and ace type of it as string = “0” ) of dacls of security descriptors of folder “c:\IBM\ITM” or not exists (trustee of it) of entries whose (trustee of it as string = “NT AUTHORITY\Authenticated Users”) of dacls of security descriptors of folder “c:\IBM\ITM”
basically this is for a Tivoli Monitoring Patch where I want to check to see if it is patched.
When the securemain utiity is done, the NT Authority\Authenticated users is added to the folder and it is also set to 1. By checking for 0 or the not existence of “Authenticated users”, I then know I need to patch. My next bit of work is to write the software distribution to push the patch. But I am very appreciative for your help as it save me a lot of time…