Remote control Peer to Peer Authorized Access After Applying following parameters settings at target “AllowP2P”, “CheckUserLogin”, “CheckUserGroup” working fine, but now requirement is suppose we creating new session request from controller by authorized domain user which are member of group “CheckUserGroup” parameter added in target parameters, and same id logged in on windows OS then id should not ask for authenticate credentials again on controller application.
- I tried Disabled “CheckUserLogin” parameter but now user not prompting for credentials, but also accepting request who is not a member of authorized group member, which we added in “CheckUserGroup” parameter
Hi aditya.vaje,
The check performed when CheckUserLogin is enabled is performed against the groups specified in CheckUserGroup as you mentioned. This is performed regardless from the current logged in user (if any).
This check doesn’t replace the Windows logon screen but it’s just an additional check for P2P sessions to allow only specific groups of users to open a session towards a Target. If the screen is locked or no user is logged on the Target machine then the Controller user have to be granted permission by the Windows logon system as usual.
So basically only if a user has performed the login on the Target machine and the screen is not locked you won’t need to enter any credentials after the CheckUserLogin popup on the Controller. In order to avoid that the property ConfirmTakeOver is typically set to “yes” to request user confirmation before establishing a session.
Dear Sir, Thanks for the reply…CheckUserGroup’ property added authorized domain group and ensured logged user enabled ‘CheckUserLogin’ property is set to ‘No’,now it is not prompting for credentials as required, but it also allows user who is not a member of CheckUserGroup added group, so it should restrict to unauthorized user, confirm takeOver is already set to yes
Hi aditya.vaje,
Keep in mind that CheckUserGroup doesn’t have any effect if CheckUserLogin is set to “no”.
This Controller prompt is only shown when CheckUserLogin is set to “yes”:
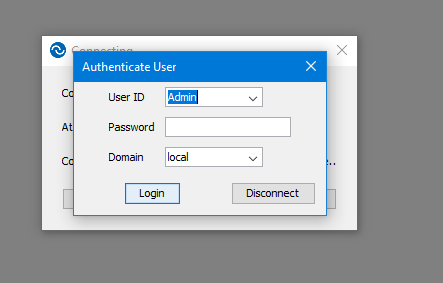
When this prompt is shown only users in the CheckUserGroup list will be authorized.
Yes Sir I understand the possibilities…but customer requires using controller by admin target system should access without password as admin already logged in locally with windows Domain id and he is authorized part of CheckUserGroup and should work like SSO, Only target user will accept incoming request.
But if we kept CheckUserLogin’ property is set to ‘No’, it is working as required but it is not validating “CheckUserGroup” authorized user and also accepting unknown other domain id’s request.
Hi aditya.vaje,
Unfortunately there is no way to use Windows session credentials and or cache or save the credentials in the CheckUserLogin popup. If you disable this check any user with a Controller can connect in P2P to whatever target.
If you need a more granular and effective way to manage sessions and permissions you need to install a Remote Control Server and import the domain users in it. These user will need to authenticate to the Remote Control Server only once in order to open a session. In this way only users authenticated to the Remote Control Server can open a session once that AllowP2P is set to no on every Target. So the CheckUserLogin popup will never been shown again but only the authorized users will have the permissions to establish a session to a Target.
With the Remote Control Server installed (known as Manged mode) you can also assign specific group of user to specific group of Targets and/or decide what policies are applied to these sessions.
Thanks for the reply sir. We have already implemented Remote Server.and it is working fine…any way we can request for the development for controller peer to peer…as a feature…till the time have raised support ticket…waiting for their reply…
You are welcome.
If you are talking about a request for enhancement you can open it here:
https://bigfix-ideas.hcltechsw.com/ideas/new
