I wasn’t suggesting it would be in this case. I was only mentioning that if your other tool stops working for some reason, BigFix could fix it. BigFix can passively monitor the health of your other tools.
The benefit is sub capacity licensing through IBM. This is the reason for ILMT. You get to pay less for IBM software by utilizing sub capacity licensing.
I’m not entirely clear what you mean by this. It is possible for a BigFix operator to have limited permissions which would prevent them from doing anything on an endpoint.
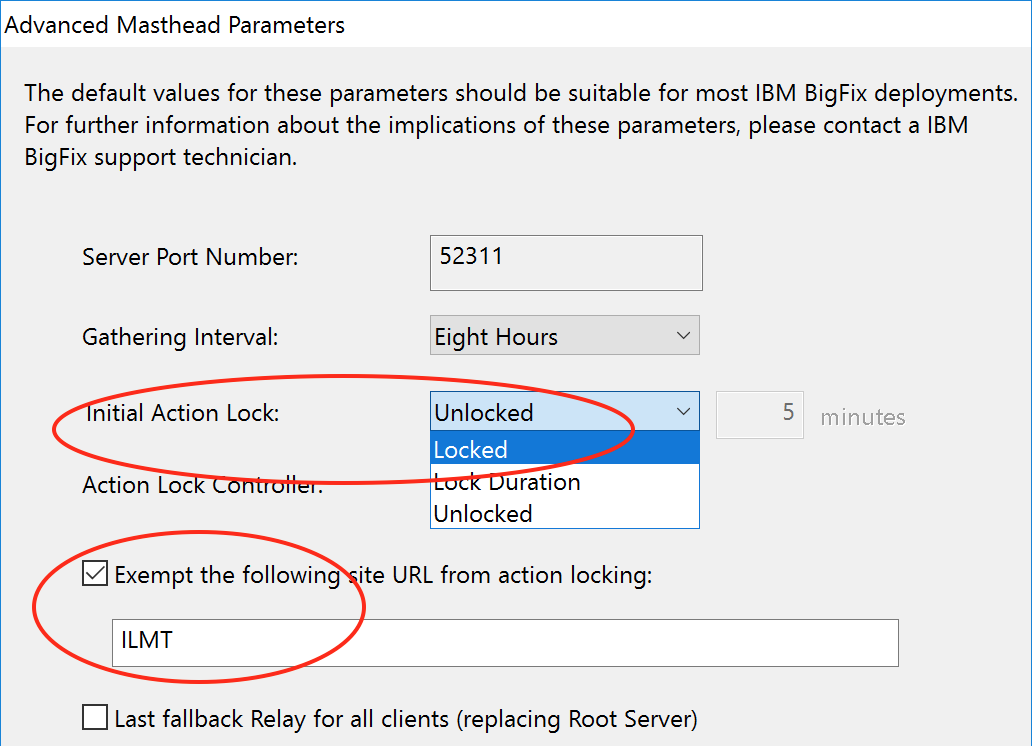
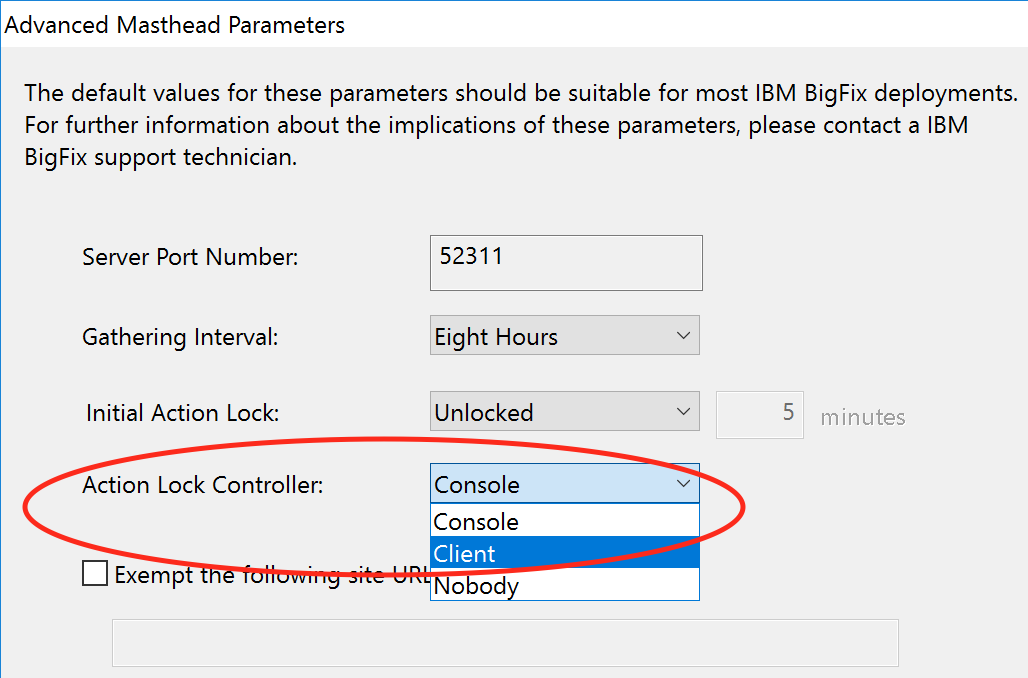
Yes, in a way there is. You can “lock” the bigfix agent for accepting actions, and you can exclude a particular site. So you could have the BigFix agents in your environment only allow processing of actions from the ILMT scanning site. This seems like part of the solution you are looking for.
I’m kind of confused at what you mean by this too.
You can give someone access to BigFix Console and WebUI but you can prevent them from creating custom content and from creating actions, at which point they DO NOT have root access to the systems that appear to them in BigFix. If however you give someone access to systems that appear in BigFix the ability to create custom content and deploy actions, then they DO effectively have root access to the systems in BigFix they can manage, though that does not have to be ALL systems in BigFix, as their scope can be limited to only the systems they SHOULD be able to manage.
I think you are confusing the scope in BigFix granted by the “Master Operator” permission vs that of a regular BigFix operator, which can be much more limited. There is also the ability to enable “4 eyes authentication” within BigFix which can either prevent an operator from taking any action at all, including a “Master Operator” or requiring 2 different operators to approve an action. One issue with “4 eyes authentication” is it ONLY works within the BigFix Console, but that doesn’t seem like an issue for your limited use case.
BigFix allows operators to have different levels of access, so some operators could have the equivalent of root access through BigFix while others would not, depending on what access you give them. This wouldn’t work if BigFix was restricted on the client side entirely, because there would NOT be a good way to give different levels of access to different operators on the BigFix side.
Another thing to consider is that access and activity within BigFix itself is easier to audit than on individual devices, unless you can already perfectly audit activity on your devices themselves, in which case you can use the same mechanism to audit what BigFix does on that system.