As we originally reported in July 2020, the “Vulnerability to Windows Systems” site has been moved to maintenance mode, and we have continued to develop the associated BigFix fixlet content. This fixlet content is generated and sourced from the Center for Internet Security’s OVAL Repository which is now hosted at GitHub - CISecurity/OVALRepo. CIS relies on a team of volunteers to contribute and generate this OVAL Repository.
Unfortunately, we have seen a significant reduction in quality updates to this repository primarily due to the lack of volunteers for this CIS community-driven project. For example, the OVAL repository has not been updated with any Microsoft Windows-related CVEs since approximately July 2022. Therefore, we see no significant updates or value in this CIS OVAL repository at this present time.
Because of this, we are announcing an abbreviated deprecation time for the “Vulnerabilities to Windows Systems” site. HCL will officially deprecate this site on December 31st, 2023. In an upcoming update to BigFix Compliance Analytics, we will no longer provide the option to import content from “Vulnerability to Windows Systems”. If users desire, they can unsubscribe and remove the “Vulnerability to Windows Systems” site from their BigFix deployment via the console.
Currently, both the “Vulnerability” and “Patch” domains within BigFix Compliance Analytics do not rely on fixlet content from the “Vulnerability to Windows Systems” site. Instead, both domains rely on the patch fixlet content enabled in your BigFix deployment (e.g., “Patches for Windows”, “Patches for RHEL”, “Updates for Windows Applications”, etc.) and/or custom sites that have been configured by customers in their deployment.
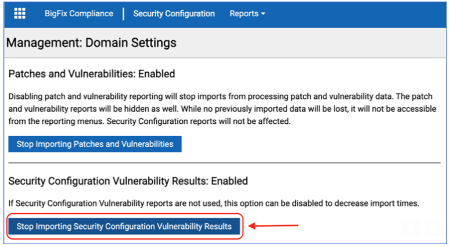
If you are actively importing “Vulnerability to Windows Systems” site within BigFix Compliance, we recommend that you disable this import. This will both improve your ETL performance and reduce confusion that can be caused by conflicting CVE reports and false positives. This can be accomplished by accessing the Management gear icon >> Domain Settings menu option and clicking on the “Stop Importing Security Configuration Vulnerability Results” (the 2nd button on the screen as highlighted in the screenshot below).