You’d add the issuer of the proxy’s certificate (which might well be built-in to the proxy itself, or might be issued by a separate internal certificate authority), but yes, if you get it in PEM format so it’s readable in notepad and has the —BEGIN CERTIFICATE---- and ----END CERTIFICATE---- strings, it really is just copy/paste onto the end of the ca_bundle.crt file.
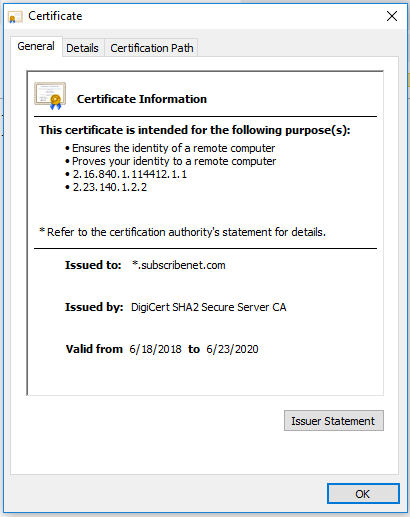
One way to tell whether they’re rewriting (which is likely, given the errors you are seeing) is to open a browser to https://gatherer.bigfix.com/ . The browser may warn about the certificate (due to mismatching the domain name, but BigFix doesn’t care about that part), and when you view the certificate, it should look like this:
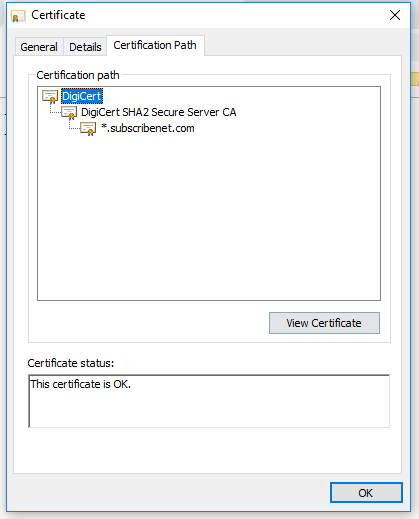
If the “Issued By” line has something else, like their own company name, then their proxy is rewriting the HTTPS connections and you’ll need BigFix to trust their issuer certificate. From this same page you would go to the “Certification Path” and select the root authority and any intermediate issuers, and hit “View Certificate” on those -
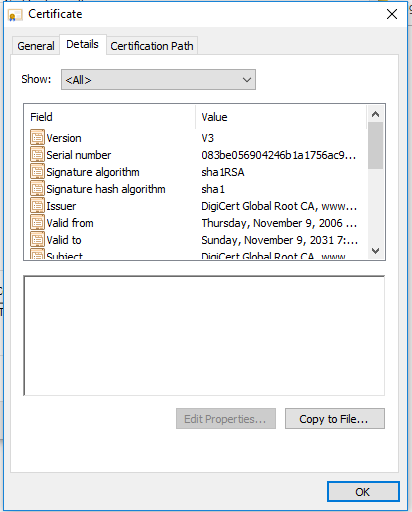
For the Root and Intermediate certificates (assuming these are custom for your company), you’d switch to the Details tab and then “Copy to File”
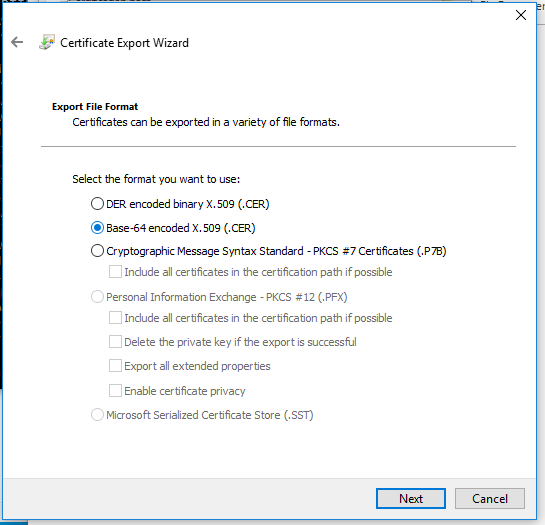
Export the certificate as a “Base64-encoded x509”:
When you’re done, each certificate should be plain-text:
C:\>type c:\temp\temp.cer
-----BEGIN CERTIFICATE-----
MIIDrzCCApegAwIBAgIQCDvgVpBCRrGhdWrJWZHHSjANBgkqhkiG9w0BAQUFADBh
MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB3
d3cuZGlnaWNlcnQuY29tMSAwHgYDVQQDExdEaWdpQ2VydCBHbG9iYWwgUm9vdCBD
QTAeFw0wNjExMTAwMDAwMDBaFw0zMTExMTAwMDAwMDBaMGExCzAJBgNVBAYTAlVT
MRUwEwYDVQQKEwxEaWdpQ2VydCBJbmMxGTAXBgNVBAsTEHd3dy5kaWdpY2VydC5j
b20xIDAeBgNVBAMTF0RpZ2lDZXJ0IEdsb2JhbCBSb290IENBMIIBIjANBgkqhkiG
9w0BAQEFAAOCAQ8AMIIBCgKCAQEA4jvhEXLeqKTTo1eqUKKPC3eQyaKl7hLOllsB
CSDMAZOnTjC3U/dDxGkAV53ijSLdhwZAAIEJzs4bg7/fzTtxRuLWZscFs3YnFo97
nh6Vfe63SKMI2tavegw5BmV/Sl0fvBf4q77uKNd0f3p4mVmFaG5cIzJLv07A6Fpt
43C/dxC//AH2hdmoRBBYMql1GNXRor5H4idq9Joz+EkIYIvUX7Q6hL+hqkpMfT7P
T19sdl6gSzeRntwi5m3OFBqOasv+zbMUZBfHWymeMr/y7vrTC0LUq7dBMtoM1O/4
gdW7jVg/tRvoSSiicNoxBN33shbyTApOB6jtSj1etX+jkMOvJwIDAQABo2MwYTAO
BgNVHQ8BAf8EBAMCAYYwDwYDVR0TAQH/BAUwAwEB/zAdBgNVHQ4EFgQUA95QNVbR
TLtm8KPiGxvDl7I90VUwHwYDVR0jBBgwFoAUA95QNVbRTLtm8KPiGxvDl7I90VUw
DQYJKoZIhvcNAQEFBQADggEBAMucN6pIExIK+t1EnE9SsPTfrgT1eXkIoyQY/Esr
hMAtudXH/vTBH1jLuG2cenTnmCmrEbXjcKChzUyImZOMkXDiqw8cvpOp/2PV5Adg
06O/nVsJ8dWO41P0jmP6P6fbtGbfYmbW0W5BjfIttep3Sp+dWOIrWcBAI+0tKIJF
PnlUkiaY4IBIqDfv8NZ5YBberOgOzW6sRBc4L0na4UU+Krk2U886UAb3LujEV0ls
YSEY1QSteDwsOoBrp+uvFRTp2InBuThs4pFsiv9kuXclVzDAGySj4dzp30d8tbQk
CAUw7C29C79Fv1C5qfPrmAESrciIxpg0X40KPMbp1ZWVbd4=
-----END CERTIFICATE-----
Copy and paste the full contents, including the ----BEGIN CERTIFICATE---- and ----END CERTIFICATE----- lines into the ca_bundle.crt. Notepad or Notepad++ work for this.
(but as always, make a backup copy of the original ca_bundle.crt before making any modifications)